
Cisco Shares Technical Details on Attacks Targeting U.S. Energy Facilities
The recent attacks aimed at energy facilities and other critical infrastructure organizations in the United States have leveraged a technique called template injection, according to Cisco’s Talos intelligence and research group.
The New York Times and Bloomberg revealed last week that the FBI and the DHS had issued a joint report warning of cyberattacks targeting manufacturing plants, nuclear power stations and other energy facilities in the U.S. and elsewhere. Unnamed officials said the attacks hit at least a dozen power firms in the United States, including the Wolf Creek nuclear facility in Kansas.
The U.S. Department of Energy said it was working with affected firms and pointed out that only administrative and business networks appeared to be impacted, not systems controlling the energy infrastructure.
Wolf Creek representatives told SecurityWeek that while they can’t make public comments on security issues, they can confirm that the attacks did not have any operational impact on the facility as control systems are completely separate from the corporate network.
According to the FBI/DHS report, the campaign has been active since at least May and an initial investigation showed that the techniques used by the hackers were similar to ones associated with a Russia-linked threat actor tracked as Crouching Yeti, Energetic Bear and Dragonfly. The group has been known to target industrial companies.
Russia has also been accused of orchestrating destructive attacks aimed at Ukraine’s power grid. Researchers have recently published an in-depth analysis of the malware believed to have been used in the latest of these attacks.
The FBI/DHS alert said the attackers sent malicious emails to senior industrial control engineers in an effort to deliver malware designed to harvest credentials and allow them to access the targeted organization’s network.
“As a class, engineering professionals may reasonably be expected to possess valuable intellectual property such as product or facility design, and have access to industrial control networks,” said Sean McBride, critical infrastructure lead analyst at FireEye.
Related: Learn More at SecurityWeek’s ICS Cyber Security Conference
The hackers reportedly also leveraged watering holes and man-in-the-middle (MitM) attacks in this campaign. McBride told SecurityWeek that the campaign has also targeted the users of government websites in other parts of the world, and some of the weaponized documents had no obvious connection to the energy sector.
Cisco Talos researchers have been monitoring these attacks and analyzed some of the malicious Word documents used by the hackers to gain access to the targeted organization’s network. The company has observed attacks aimed at critical infrastructure firms around the world, but the primary targets appear to be the United States and Europe.
The malicious documents, disguised as resumes and environmental reports, don’t rely on traditional methods, such as VBA macros or other embedded scripts, to deliver malware. Instead, when the decoy document is opened, while the Word application is in progress of being launched, a template file is loaded from an attacker-controlled SMB server.
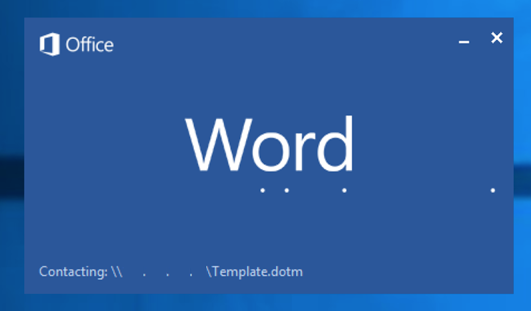
Loading the template file in what is known as a template injection attack allowed the attackers to silently harvest SMB credentials. The method can also be used to download other malicious payloads to the victim’s device, but the hackers’ SMB server was offline during Talos’ analysis and experts could not determine what other payloads may have been served.
Researchers have found a connection between the template injection used in this attack and an open source tool named Phishery. It’s unclear if the similarities are a coincidence, if the hackers behind the energy sector attacks modified the existing tool, or if they simply wanted to confuse investigators.
“We believe this campaign is likely designed to steal information enabling the attackers to gain future access to industrial control systems that run this critical infrastructure, rather than an espionage-type campaign designed to steal plans and other sensitive commercial information,” said Galina Antova, co-founder of Claroty, a cybersecurity company specialized in protecting industrial control systems.
Related: The Threat to Critical Infrastructure – Growing Right Beneath Our Eyes
Related: Critical Infrastructure Security – Risks Posed by IT Network Breaches











