Target Corporation on Wednesday said that the attacker(s) behind the recent massive data breach at the retailer likely compromised its systems by using stolen credentials from a vendor.
“We can confirm that the ongoing forensic investigation has indicated that the intruder stole a vendor’s credentials which were used to access our system,” a Target spokesperson told SecurityWeek in a emailed statement.
The company did not say what vendor or what platform was compromised using the stolen credentials.

Earlier this month, Target CEO Gregg Steinhafel confirmed that point-of-sale (POS) malware was used in the recent attack that compromised millions of credit and debit card account numbers of customers across the country, but since then the company has remained relatively silent.
According to a source who spoke to the Wall Street Journal, systems accessed by the attacker accessed and payment systems appeared to have no relation to each other.
However, security researcher and blogger Brian Krebs shared some details he discovered as part of his ongoing coverage of the breach. According to Krebs, an analysis of a piece of malware believed to used in the attack was likely responsible for exfiltrating stolen data from the compromised POS systems to a central shared drive.
That sample, which was submitted to Symantec’s ThreatExpert service on Dec. 18, 2013 16:08:11, showed (PDF) the malware attempts to leverage the account user name “Best1_user” and password “BackupU$r” to access the shared drive.
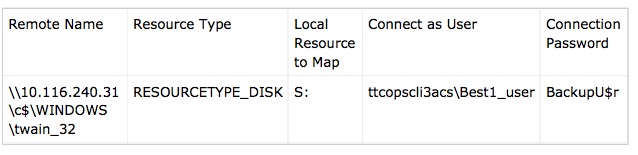
Krebs shed some insight into that user name and its connection to a software platform that the hackers likely targeted during one stage of their attack:
That “Best1_user” account name seems an odd one for the attackers to have picked at random, but there is a better explanation: That username is the same one that gets installed with an IT management software suite called Performance Assurance for Microsoft Servers. This product, according to its maker — Houston, Texas base BMC Software — includes administrator-level user account called “Best1_user.”
This knowledge base article (PDF) published by BMC explains the Best1_user account is installed by the software to do routine tasks. That article states that while the Best1_user account is essentially a “system” or “administrator” level account on the host machine, customers shouldn’t concern themselves with this account because “it is not a member of any group (not even the ‘users’ group) and therefore can’t be used to login to the system.”
A BMC spokesman told The Star Tribune that he couldn’t discuss Target’s comments or Krebs’ assertions. “BMC Software has received no information from Target or the investigators about this matter,” he told the Tribune.
An analysis report (PDF) by Dell SecureWorks’ Counter Threat Unit (CTU), released to some its clients and obtained by Krebs, also provided some insight as to how the attackers executed at least part of the operation.
“Once inside, the attackers used multiple tools to eventually gain access to POS systems,” the CTU report said. “The presence of tools such as PsExec and System Center Orchestrator may indicate the use of Windows networking, credentials, and systems management tools to ultimately upload the POSRAM Trojan horse on POS systems.”
If the attackers did use credentials to gain access to user accounts, the Target attack is yet another example of attackers leveraging privileged accounts to successfully compromise an organization. Theft, misuse, and exploitation of privileged accounts is a key tactic in each phase of APTs and other targeted attack campaigns, according to a report from CyberSheath released last year.
“The majority of breaches involve lost or stolen credentials, as we’re hearing was the case with the Target compromise,” Trey Ford, global security strategist at Rapid7, told SecurityWeek. “In most of these cases, organizations don’t know they’ve had an account compromised until it’s far too late and the damage is done. In the case of an organization like Target, you’re looking at an extremely complex environment with hundreds of thousands of employees, systems, sites, and vendors; every aspect represents some level of risk.”
“The problem is that it’s impossible to make every one of those elements bulletproof and traditional incident detection systems aren’t looking for deceptive activity,” Ford said. “Attackers left undetected for a sufficient amount of time can do just about anything they want.”
According to Verizon’s 2013 Data Breach Investigation Report, 76 percent of network intrusions exploited weak or stolen credentials.
Many questions still remain, but as new details about the attack against Target emerge, one thing is clear—these attackers were highly skilled and determined, and it’s highly unlikely that Target Corp. was the only company they hit.
“The Target compromise demonstrates that cybercriminals can conduct operations that involve intrusion, lateral movement, and data exfiltration in complex retail networks that are designed to meet PCI-DSS requirements,” the SecureWorks’ CTU report continued. “The malware analyzed by the CTU research team shows that the attackers could adapt their attack techniques to the unique circumstances of Target’s environment. This level of resourcefulness points to the current value for credit card data in the criminal marketplace, and similar breaches will be common until fundamental changes are made to the technology behind payment cards.”
Attorney General Eric Holder said on Wednesday that Authorities are committed to hunting down the hackers behind the massive data breach.
“I can confirm the department is investigating the breach involving the US retailer, Target,” Holder said at a Senate Judiciary Committee hearing. “And we are committed to working to find not only the perpetrators of these sorts of data breaches — but also any individuals and groups who exploit that data via credit card fraud.”














