Steven Spielberg certainly knows how to leave an indelible impression. So much so that when I see the words “DDoS attacks,” I also see a big ol’ Great White and can’t help but hear John Williams’ infamous score.
Dun dun . . . dun dun . . .
Slow and low. A harbinger of destruction, building to that still freakishly creepy crescendo.
Da na nah!
Not unlike when a shark stalks and attacks its unsuspecting prey, some DDoS attacks can come with a sudden full-force rush. However, quite unlike shark attacks (last year, there were 80 unprovoked shark attacks reported worldwide), DDoS attacks already number in the thousands per day. And no one is impervious to them.
A Brief History of DDoS
The history of DDoS may not be a long one, but it’s a rapidly evolving—and even exploding—one. What began in 1999 with plots to extort funds via botnet attacks (i.e., criminals promised to take down websites if funds were not paid) has evolved to include competitive, political, and, even, “just because I can” egotistical motivators.
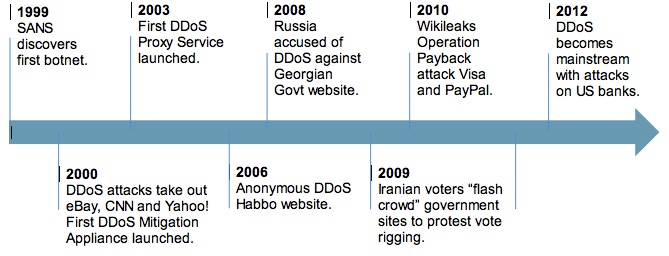
Today, DDoS attacks have become much more sophisticated, potent, and difficult to detect thanks to new multi-faceted and diversionary tactics. And they’re everywhere. In the past two years, no area of commercial or government activity has dodged the DDoS bullet.
Even more concerning is the use of DDoS as a smokescreen for attacks likely to cause even more damage.
Take for example the 2011 Sony PlayStation attack. The Sony IT team thought they were dealing with a single attack vector and while they were running around trying to get their services back up, they missed the SQL injection. This diversionary ploy resulted in the theft of 100 million user accounts and credit card details, and cost Sony more than $200 million.
Bank of the West became another noteworthy victim. Hackers infected a number of the bank’s clients with a Zeus Trojan, but then sat back and waited for the perfect time to activate it. That time was Christmas Eve, when the hackers DDoS’d the heck out of the bank. While the IT security team was in a mad panic trying to protect against the DDoS attack, the hackers triggered the Trojan and, in a matter of minutes, successfully lifted nearly $1 million. No one was the wiser until it was too late. Merry Christmas, baby!
Great Whites vs. Tigers—Which Is Most Dangerous?
So where and how do you defend? We’ve been seduced into thinking the volumetric (Great White) attacks are commonplace. Certainly, they’re not to be ignored, but like a true Great White shark attack on a human, they really don’t happen as often as we’ve been led to believe.
Rather, it’s the ones more akin to Tiger sharks that we should be most wary of. See, Tiger sharks are often elusive. They swim slowly. They hunt in shallow waters. And their cryptic coloring makes it difficult for prey to detect them. In a sense, they fall under the radar, just as slow-and-low DDoS attacks do.
While volumetric attacks, which show spikes in incoming packet rates of ten thousands to more than one million per second, continue to increase in size, the number of these incidents is only increasing at a moderate rate. In a sense, the volumetric attacks (e.g., the record-breaking Spamhaus attack that garnered much media buzz) have become a smoke screen for the slow-and-low attacks, which, by contrast, come in many different guises and have been growing in popularity for the past three years. They target back-end weaknesses and aim to make network resources busy. And because they cannot be detected using the previous volumetric approach, they can take out large websites with as few as 40 http requests per second.
A Bigger, Broader Boat
You can’t stop DDoS attacks from happening, but you do have choices in how to defend and mitigate against them.
First, you could choose to do nothing. But that’s kind of like throwing a bag of chum around your neck in shark-infested waters and praying that once you’re attacked some hunk of a lifeguard will come to your rescue.
Another choice would be to supersize—meaning upgrade everything in the data path to the point it’s impossible to flood the bandwidth or servers. But that’s somewhat like trying to haul a tank onto an already capsizing paddle boat. Not only would it be expensive (and a bit wasteful), but it also wouldn’t do much to defend against the slow-and-low Tigers. It’s those sneaky snipers who don’t even need to pierce your armour because they’ve found their way in through an open back door.
Next, there’s the silver bullet. As none exists today, this choice involves a whole lot of hoping and finger crossing.
Or you could think of investing in a more sensible, but well-appointed, approach that addresses volumetric attacks and is able to detect the application-level attacks that often get lost in the noise. This approach requires continually monitoring and logging all inbound and outbound Web traffic to detect unusual activity coming from a user and then intelligently respond in real time by dropping suspect or noncompliant traffic as soon as the optimum performance from critical applications begin to degrade.
The DDoS shark is well and truly out of its cage, and it’s not going back inside anytime soon. How prepared are you for the feeding frenzy?















