Stuxnet Version 0.5 Targeted Crucial Valves that Feed Uranium Hexafluoride Gas Into Centrifuges
SAN FRANCISCO – RSA CONFERENCE 2013 – Symantec’s Francis deSouza addressed a packed conference hall on Tuesday morning, and kicked off his RSA Conference keynote by sharing details on new intelligence from Symantec on the earliest known version of Stuxnet—a previously undiscovered version that featured an entirely different attack mechanism than its successors.
Timed to coincide with deSouza’s keynote, Symantec also published a white paper on the research, sharing additional details on its recent discoveries.
Originally discovered in the summer of 2010, Stuxnet is widely known to have targeted centrifuges at the Natanz nuclear facility in Iran, with the goal of slowing the nation’s production of enriched uranium.
Now, Symantec’s research has determined that other parts of the facilities could have been targeted, or that the earlier version of the infamous cyber weapon at least had the capabilities to target other industrial components at Natanz.
According to Symantec, Stuxnet Version 0.5, an earlier and less sophisticated version of Stuxnet, was designed to close crucial valves that feed uranium hexafluoride gas into the centrifuges, causing serious damage to the centrifuges and the uranium enrichment system as a whole.
While Stuxnet 0.5 may not have had as many bells and whistles as its predecessor, it was still complex and powerful nonetheless.
“The attack essentially closes the valves causing disruption to the flow and possibly destruction of the centrifuges and related systems,” Symantec researchers noted in a blog post. “In addition, the code will take snapshots of the normal running state of the system, and then replay normal operating values during an attack so that the operators are unaware that the system is not operating normally. It will also prevent modification to the valve states in case the operator tries to change any settings during the course of an attack cycle.”
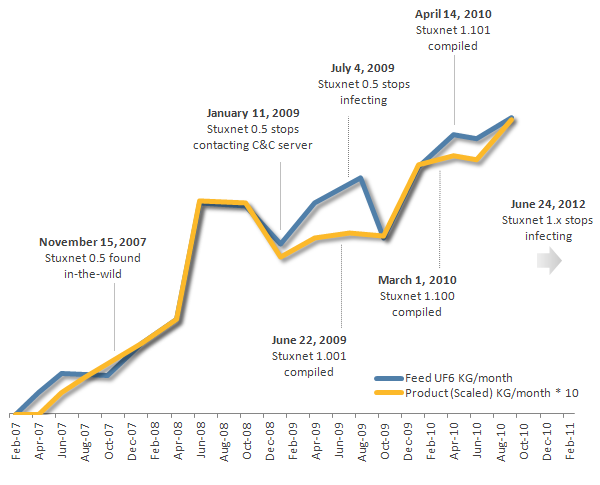
Symantec’s research on Stuxnet Version 0.5 suggests that the Stuxnet project as a whole could possibly date back to 2005 or earlier, as a Command and Control (C&C) server associated with version 0.5 was registered in November 2005. When Stuxnet 0.5 began circulating in the wild is unclear, Symantec said.
Rather than affecting the speed of uranium enrichment centrifuges, Stuxnet 0.5 was designed to close crucial valves that feed uranium hexafluoride gas into the centrifuges, causing serious damage to the centrifuges and the uranium enrichment system as a whole.
Known to have been developed or backed by the United States, more versions of Stuxnet are known to exist, but have never been recovered, Symantec said. Interestingly, Symantec did discover that the date Stuxnet 0.5 stopped compromising systems was July 4, 2009—just 12 days after version 1 was created.
Similar to any successful software project, Stuxnet became more sophisticated and more aggressive over time.
Different PLC Targets
Stuxnet version 1 targeted Siemens 315 PLCs, which controlled the spinning centrifuges at Natanz, while version 0.5 attacked Siemens 417 PLCs to modify the valve operation during uranium enrichment.
According to Symantec, Stuxnet 0.5 only contains the 417 PLC attack code and does not contain the 315 attack code.
“Key parts of the 417 attack code missing from versions 1.x is fully implemented in Stuxnet 0.5,” Symantec’s report explained. “This demonstrates that the 417 attack code was the first attack strategy implemented by Stuxnet. This original 417 attack code attempted to modify valve states during the uranium enrichment process at Natanz, Iran, to cause damage to the centrifuges and the system as a whole.”
In terms of development, Symantec researchers noted that some components of Stuxnet 0.5 were created using the Flame (or Flamer) platform, whereas 1.x versions were based mainly on the Tilded platform.
Back in June 2012, Kaspersky Lab researchers came forward with evidence that they said “proves without a doubt, that the ‘Tilded’ platform is indeed connected to the Flame platform.”
While there is a connection, Symantec’s report reiterated previous assumptions that because of the code base, Flamer and Tilded platforms are completely different platforms, with two separate development teams behind them.
Over time, the developers appeared to have migrated more towards the Tilded platform, Symantec said, noting that the malware creators re-implemented Flamer-platform components using the Tilded platform in later versions.
Detailed information from Symantec on Stuxnet 0.5 can be found in the white paper, Stuxnet 0.5: The Missing Link.
The video below from Symantec also provides additional information.
















