Stuck On Stuxnet – Are Grid Providers Prepared?
The Stuxnet virus seemingly just won’t go away, nor the widespread media of coverage of it, driven by the fact that it has some of the most doomsday-like attributes of any attack that we’ve ever seen reported.
Just think about it; it’s honestly hard to recall the last major malware attack so threatening that it seeped over from the world of IT security experts into the mainstream environment at all.
As a society we’ve become so desensitized to the ever growing range of cyber-threats that unless they’re named after a skanky celebrity or use some sneaky new social engineering scheme, most people never even hear about them much anymore.
But a persistent threat designed to attack nuclear power stations, and, in at least one case, those located in Iran of all places? It’s truly the stuff that Hollywood thrillers are made of.
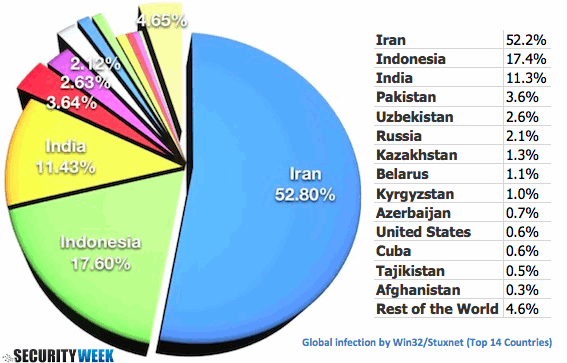
And lest anyone should think that Stuxnet is something that only Iran has to be concerned with, unfortunately they’d be painfully wrong. Not only will U.S. grid infrastructures see more of these types of campaigns, most experts seem to think that energy providers and other key backbone constituencies are woefully unprepared to ward off such assaults.
The primary reason for this is that grid infrastructure providers have always been far more concerned with walling off their physical assets than worried about malware, but with the increasing adoption of SCADA systems that offer remote management capabilities delivered via Internet connectivity, and the arrival of real attacks like Stuxnet, the notion of shutting down, disrupting or damaging a power plant or even the water supply from behind a computer located halfway around the world has evolved from the realm of theoretical to the very real.
Just how unprepared for this are utilities providers and the companies that make SCADA technologies? Not that long ago when I was working with my vulnerability researcher colleagues at Core Security and they found a pretty nasty bug in a piece of widely used SCADA software, they couldn’t even find anyone at the involved vendor to take their call and listen to their findings. The notion of handling security vulnerabilities, let alone dealing with targeted malware attacks, was not even on their radar.
Related Reading – The Increasing Importance of Securing The Smart Grid
I recently had the opportunity to sit down with a state CISO and hear his thoughts about the readiness of U.S. grid providers to respond to the arrival of threats like Stuxnet. This CISO, who is a nationally recognized leader in pushing proactive security measures, told me that he was very concerned about what he was hearing and seeing from his state’s energy companies. Some companies he had spoken with had a pretty good fix on preventing their operations from being remotely compromised, however, others were vastly unready to prepare for future attacks, he said.
Part of the problem, said the CISO, was that grid providers have never been known as particularly innovative in seeking out ways to assess their IT security exposures in general and that very few have taken aggressive or proactive measures to understand precisely where they might be exposed.
 Another issue was that people like himself, namely government oversight, have traditionally had very limited ability to test the security effectiveness of these private sector firms to discern how well they could react to such a campaign.
Another issue was that people like himself, namely government oversight, have traditionally had very limited ability to test the security effectiveness of these private sector firms to discern how well they could react to such a campaign.
This particular CISO is actually using Stuxnet as a means to press private utilities and other providers into the adoption of more comprehensive and highly scrutinized IT security practices, but he maintained that the only reason he’d been able to do so is because he’s spent a lot of time gathering high-level federal security clearances, without which he said your average government security leaders may not be able to goad private companies into responding.
Obviously, this fact, and the lack of proper security response operations within some of the technology providers power companies deal with, lies at the heart of the problem.
It’s true that some efforts to change this are underway, pushed along by standards such as the NERC CIP mandate, which requires grid providers to test and validate some of their security controls and prove their effectiveness to outside auditors. However, even that standard seems fairly limited, and certainly nascent.
For just as long as I can remember, we’ve been hearing people from both the government and private sectors argue that the other side needs to be more forthcoming with information sharing if progress is to be made in improving national IT security in general.
Let’s all hope that Stuxnet is the type of phenomenon that brings the two sides together to get serious about doing as good a job as possible in preventing such threats… before the lights go out.
Related Reading – The Increasing Importance of Securing The Smart Grid














