A team of researchers has identified what appears to be a new method that malicious actors could use to trick users into connecting to their wireless access points (APs).
The method, dubbed SSID Stripping, was disclosed on Monday by AirEye, which specializes in wireless security. It was discovered in collaboration with researchers at the Technion – Israel Institute of Technology.
According to the researchers, SSID Stripping affects devices running Windows, macOS, Ubuntu, Android and iOS. They showed how an attacker could manipulate the name of a wireless network, specifically the SSID (Service Set Identifier), so that it’s displayed to the user with the name of a legitimate network.
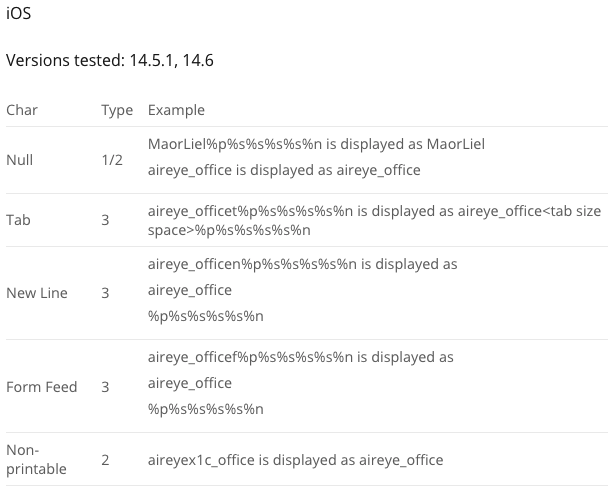
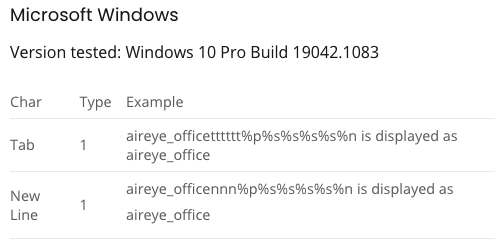
They were able to generate three types of what they describe as “display errors.” One of them involves inserting a NULL byte into the SSID, causing Apple devices to display only the part of the name that is before this byte. On Windows devices, the attacker could use “new line” characters to achieve the same effect.
Another type of display error — these appear to be the most common — can be triggered using non-printable characters. An attacker can add special characters to the SSID that will be included in the name, but will not actually be displayed to the user.
“For example, the network name ‘aireye_x1cnetwork’ (with x1c representing a byte with the value 0x1C hex), is displayed exactly the same as ‘aireye_network’,” the researchers explained.
The third type of display error involves pushing out a certain part of the network name from the visible portion of the screen.
“For example, an SSID of the form ‘aireye_networknnnnnnnnnnnrogue’ (where ‘n’ denotes the New Line character) may be displayed by an iPhone as ‘aireye_network’ since the word ‘rogue’ is pushed out of the display,” the researchers said. “Together with type 2 errors this can be used to efficiently hide the suffix of a rogue network name.”
The threat posed by SSID spoofing has been known for many years. If an attacker can convince a user to connect to their own Wi-Fi connection, they may be able to intercept the victim’s communications and steal their data.
Attacks often involve the attacker setting up a rogue AP that has the same name as a connection typically used by the target. However, operating system vendors have implemented protections designed to prevent users from unwittingly connecting to rogue APs by matching not only the name of a connection but also other attributes before automatically connecting to it.
In an SSID Stripping attack, the user would see a connection whose name matches a connection they trust, but they would have to manually connect to it for the attack to work. On the other hand, this bypasses the aforementioned security controls since the device processes the actual name of the SSID — the string that the attacker has entered, not what the victim sees on the screen — and does not prevent the victim from connecting to the rogue AP.
The researchers described their findings as a vulnerability, but impacted vendors don’t seem to view it as a serious security issue. AirEye said the findings were reported to Apple, Microsoft, Google (Android) and Canonical (Ubuntu) in July. While they all acknowledged the issue, they classified it as having “minor security implications” and they are unlikely to implement patches anytime soon.
“Enterprises must realize that there is more to Wi-Fi security than setting the correct authentication method,” AirEye said in its blog post. “Wireless capable devices are exposed to many threats that are related to the open nature of the medium – everyone can send frames into the air and every device with wireless capabilities is constantly processing such frames. Attackers can exploit the Wi-Fi medium in order to bypass existing network security controls and gain access to enterprise networks through vulnerable wireless devices. It is time for corporations to consider solutions for monitoring, controlling and protecting the network airspace around them.”
AirEye has released a free tool that can be used by organizations to assess the susceptibility of corporate devices to SSID Stripping attacks.
Related: Apple Quietly Patched 0-Click Wi-Fi Code Execution Vulnerability in iOS
Related: iOS Security Update Patches Recently Disclosed Wi-Fi Vulnerability














