Majority of Attacks in 2012 Were Redirects from Legitimate Sites, 27 Percent of All Cybercrime Linked to ‘Blackhole’ Exploit Kit
Even though organizations are increasingly focusing on mobile devices and security, cyber-criminals still focused on traditional malware and Web-based attacks in 2012, Sophos found in its latest threat report.
More than 80 percent of attacks in 2012 were redirects, and the majority of those redirects were from legitimate sites that had been hacked, Sophos found in its Security Threat Report 2013, released Tuesday. The BlackHole exploit kit also accounted for 27 percent of exploit sites and redirects in 2012, Sophos found.
BlackHole is used by cyber-criminals to deliver a wide variety of malicious payloads, including Trojans such as Zeus, fake antivirus, and other types of malware for Windows, Linux, and Mac computers. “It is and equal-opportunity victimizer,” the report found. The latest version of the toolkit was released over the summer and includes well-known attacks that have a high success rate. BlackHole, and other such tooklits, is a “potent cocktail of a dozen or more exploits,” Sophos said.
 “The web remains the dominant source of distribution for malware—in particular, malware using social engineering or targeting the browser and associated applications with exploits,” Gerhard Eschelbeck, CTO of Sophos, wrote in the report’s foreword.
“The web remains the dominant source of distribution for malware—in particular, malware using social engineering or targeting the browser and associated applications with exploits,” Gerhard Eschelbeck, CTO of Sophos, wrote in the report’s foreword.
Sophos predicts there will be more premium features, such as scriptable Web services, APIs, and malware quality assurance platforms, built-into BlackHole for even more complex attacks.
Sophos observed criminals were using public key infrastructure (PKI)-grade encryption to lock up user files in rogueware scams. The malware encrypts the files on the user’s computer and demands the user pay a ransom to get the files back. These types of “irreversible malware” are typically delivered using standard drive-by techniques built by an exploit kit, such as BlackHole, according to the report.
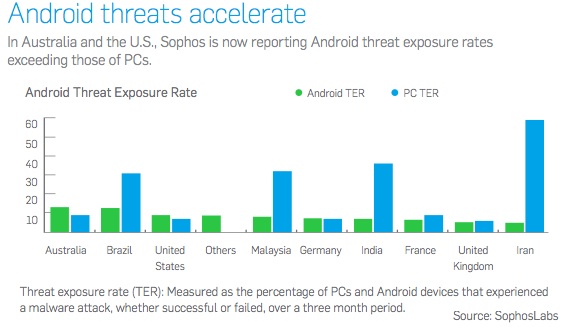
Attackers have expanded their attacks beyond the Windows platform to include Mac OS X and Android, the report found. “2012 was a year of new platforms and modern malware,” Sophos wrote.
Even though the overall market share for Mac OS X remains small compared to other platforms, the number of Mac threats are growing as more users switch. Flashback, the malware that reportedly infected hundreds of thousands of Apple systems in April was the largest mass attack this year, but it’s not the only Mac malware out there. In a typical week, SophosLabs detects 4,900 pieces of OS X malware on Mac computers. In a snapshot of Mac malware detected over a one-week period in August, SophosLab detected various variants of fake antivirus, codecs and Flash player.
Android has become “today’s biggest target,” the report said, noting that fake apps that secretly send messages to premium rate SMS services are currently the most common type of Android malware affecting users.
Riskiest Countries
Sophos rated Hong Kong, Taiwan, United Arab Emirates, Mexico, and India the riskiest countries for experiencing a malware attack. Norway, Sweden, Japan, the United Kingdom, and Switzerland were rated the safest.
State-sponsored cyber-attacks also made it in the report, with Sophos noting that it was difficult to prove any country was behind a cyber-attack. “By their very nature, state-sponsored cyber attacks (and attacks by highly-sophisticated private teams closely allied with states) are difficult to track and prove—and equally susceptible to being overhyped,” said Sophos.
However, the report was quick to point out that more and more countries now have the capability to sanction cyber-war. “Nevertheless, more actors appear to be developing the capability to execute such attacks. And, once they possess such a capability, the temptation to use it will be substantial,” the report concluded.
The increased availability of malware testing platforms will make it more likely for malware to slip through traditional business security systems and be able to hide within corporate networks for a sustained period of time, Sophos said in the report. Sophos also noted that with GPS and NFC becoming more integrated into mobile platforms, new attacks targeting those technologies may be on the horizon.
“Two of the defining terms of 2012 are ‘empower’ and ‘evolve.’ Attacks and threats—on PCs, Macs and mobile devices—continue to evolve as does the technology to combat them,” Eschelbeck said.
The full report can be downloaded from Sophos here in PDF format.















