Law enforcement, cybersecurity companies, Google and other tech firms have worked together on dismantling a sophisticated ad fraud scheme that earned its operators tens of millions of dollars.
The results of a campaign against cybercriminals specializing in ad fraud were announced on Tuesday, when Google and WhiteOps published a white paper describing a complex scheme, and the U.S. Department of Justice unsealed indictments against eight individuals.
Google and WhiteOps led the campaign, but they had help from several other individuals and organizations, including Adobe, Amazon, CenturyLink, ESET, Facebook, Fox-IT, F-Secure, Malwarebytes, Microsoft, McAfee, Oath, Proofpoint, The Shadowserver Foundation, Symantec, The Trade Desk, Trend Micro and Matt Carothers.
The ad fraud scheme disrupted by law enforcement and the tech industry has been dubbed “3ve.” The name stems from the fact that the operation was composed of three sub-operations, each using different techniques.
In the digital advertising ecosystem, publishers often auction the ad space available on their websites and advertisers bid on that ad space based on the potential interest of the site’s visitors. While this system is very efficient for both publishers and advertisers, it’s also a very attractive target for fraudsters and cybercriminals, as demonstrated by the numerous schemes uncovered in the past years.
Fraudsters can make a significant profit by tricking advertisers into thinking that their ads are displayed on the sites of premium publishers and they are seen by many real users.
The individuals behind 3ve used one million compromised IP addresses, over 10,000 fake websites, and more than 60,000 accounts selling ad inventory to trick businesses into paying them roughly $29 million. Investigators estimate that 3ve generated over 3 billion ad bid requests every day.
The cybercriminals used malware such as Kovter and Miuref (Boaxxe) to take control of computers and generate fake ad views.
One of the 3ve sub-operations focused on video fraud. The fraudsters set up fake websites and tricked advertisers into buying ad space on these sites for their videos. They used hijacked IPs and computers as proxies for their activity, which allowed them to keep their bot software isolated. The attackers used BGP hijacking to obtain 200,000-500,000 IP addresses from enterprise data centers and a botnet of roughly 5,000 user devices infected with Miuref/Boaxxe malware to drive traffic to their sites.
The second 3ve sub-operation involved 700,000 Windows computers infected with Kovter malware and a browsing module designed to access the counterfeit websites in a way that mimicked human behavior. For example, the module could perform mouse movements and clicks, play media content on a webpage, and access legitimate websites such as Facebook in an effort to avoid raising suspicion.
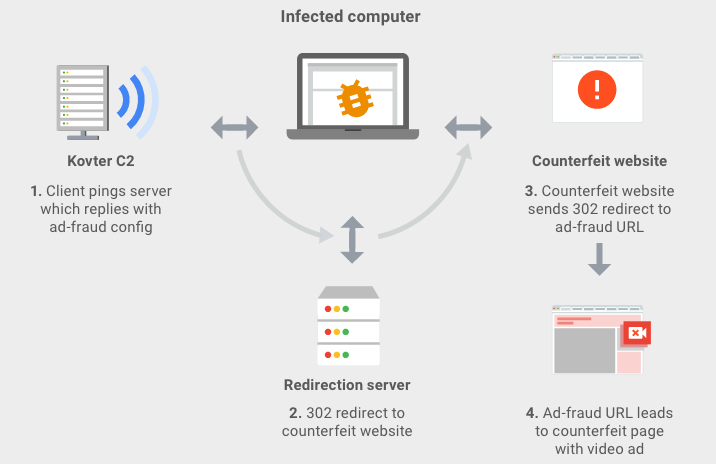
The third sub-operation was similar to the first as it also leveraged compromised data center IPs, but relied on other data center IPs to cover its tracks instead of user computers.
3ve takedown and indictments
After monitoring the cybercrime scheme for several months, a coordinated effort was launched to disrupt the 3ve infrastructure. According to WhiteOps and Google, bid request traffic associated with the scheme almost completely disappeared within 18 hours after the takedown operation started. The takedown involved sinkholing 23 domains and executing search warrants at 11 different companies in the US for 89 servers.
One Russian, Aleksandr Isaev, and two Kazakh nationals, Sergey Ovsyannikov and Yevgeniy Timchenko, were indicted by the U.S. Justice Department for their role in running the 3ve operation. Ovsyannikov was arrested last month in Malaysia and Timchenko was arrested earlier this month in Estonia. They both await extradition to the United States.
The Justice Department also announced charges against Aleksandr Zhukov, Boris Timokhin, Mikhail Andreev, Denis Avdeev, and Dmitry Novikov. They are all Russian nationals accused of running an ad fraud operation tracked as Methbot, which WhiteOps first detailed in late 2016. The Methbot operation is estimated to have earned fraudsters over $7 million.
Of the Methbot suspects, Zhukov was arrested earlier this month in Bulgaria. The rest remain at large.
Related: Google Blocks New Ad Fraud Scheme
Related: U.S. Disrupts Russian Botnet of 500,000 Hacked Routers















