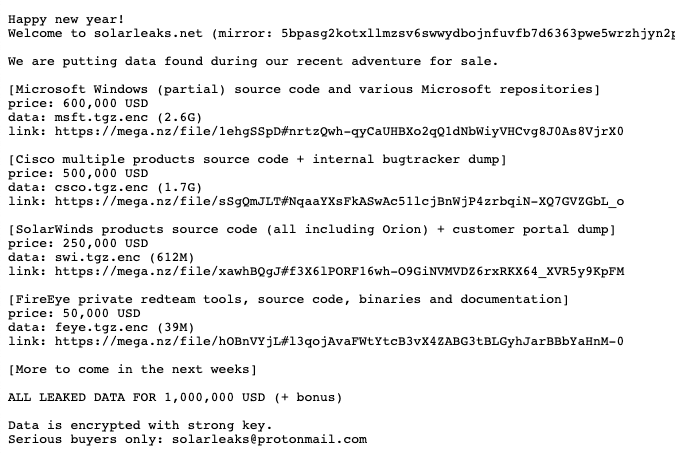
Someone has set up a website named SolarLeaks where they are offering to sell gigabytes of files allegedly obtained as a result of the recently disclosed SolarWinds breach.
The SolarLeaks website offers source code allegedly obtained from Microsoft, Cisco, SolarWinds and FireEye. The information allegedly taken from Microsoft, offered for $600,000, is contained in a 2.6 Gb file and the seller claims it includes partial source code for Windows and “various Microsoft repositories.”
The files allegedly originating from Cisco, offered for half a million dollars, include 1.7 Gb worth of product source code and a dump of the networking giant’s internal bug tracker, the seller claims. For $250,000, the seller claims to offer 612 Mb worth of source code for SolarWinds products and information taken from the company’s customer portal.
In the case of FireEye, the seller claims to offer the red team tools that FireEye confirmed to have been stolen as a result of the SolarWinds breach, as well as source code, binaries and documentation. The FireEye files are offered for $50,000.
The people who set up the SolarLeaks website claim they are willing to sell all files for $1 million, and they also claim they still have access to the systems of targeted companies and this is only the first batch of data. They also claim they can provide proof that their offer is legitimate.
SecurityWeek has attempted to reach out to the hackers for this proof, but emails are not being delivered to the email address they have shared. This email address currently appears to be the only contact information shared by the hackers.
Microsoft did confirm recently that it was targeted by the SolarWinds attackers and admitted that they gained access to some source code, but the tech giant claimed the incident did not represent a security risk to services or customer data. SecurityWeek has reached out to Microsoft and will update this article if the company shares any information.
Continuous Updates: Everything You Need to Know About the SolarWinds Attack
Cisco said it was aware of the SolarLeaks website, but claimed it “has no evidence at this time of any theft of intellectual property related to recent events.” The company admitted that SolarWinds products were found on a “small number” of its systems, but said it did not use SolarWinds solutions for enterprise network management.
“At this time, there is no known impact to Cisco products, services, or to any customer data,” Cisco said in an advisory.
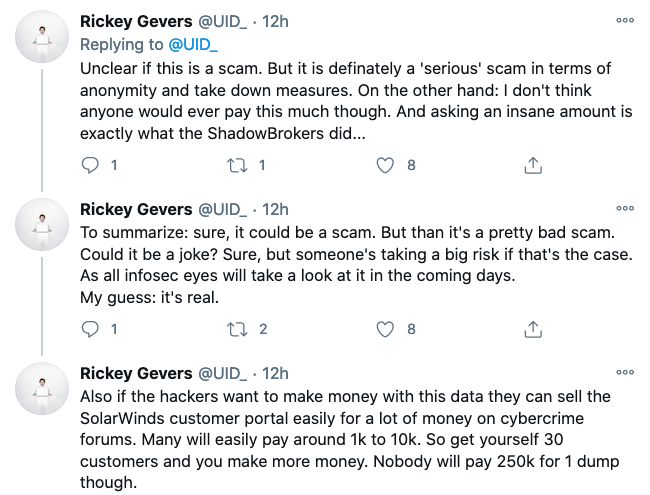
While some members of the cybersecurity industry believe SolarLeaks is likely a scam, others believe the seller could really possess the files they are offering.
Security expert Rickey Gevers noted on Twitter that the domain of the SolarLeaks website was registered very recently through Njalla, which describes itself as a privacy-aware domain registration service.
“Njalla is a preferred registrar from Fancy Bear and Cozy Bear. This alone already shows the people behind this website have at least a little knowledge about Russian MO,” Gevers said, noting that SolarLeaks appears to be mimicking Shadow Brokers, a group that a few years ago sold and leaked hacking tools stolen from the NSA.
“To summarize: sure, it could be a scam. But then it’s a pretty bad scam. Could it be a joke? Sure, but someone’s taking a big risk if that’s the case. As all infosec eyes will take a look at it in the coming days. My guess: it’s real,” Gevers wrote.
Jake Williams, founder of Rendition Infosec and a respected member of the cybersecurity industry, noted that “we’ve seen Russian threat actors use this type of misdirection before to muddy attribution” and urged people not to fall for it.
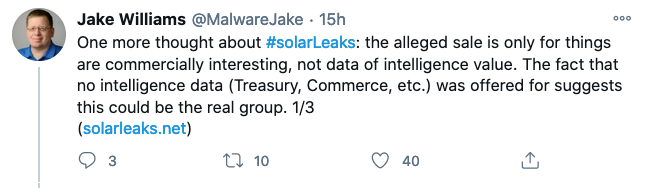
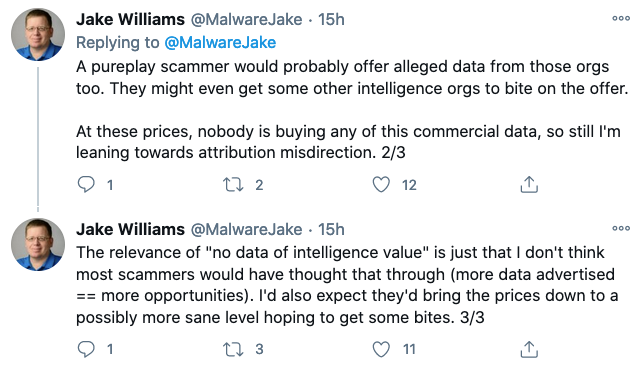
While SolarWinds and cybersecurity companies have so far refrained from attributing the supply chain attack to a known threat actor, the U.S. government believes the operation was likely conducted by Russia, allegations that Moscow has denied. Kaspersky reported this week that it found similarities between the Sunburst malware used in the SolarWinds attack and a piece of malware previously attributed to Russian cyberspies.
An attack timeline published this week by SolarWinds confirmed that the attackers gained access to its systems more than one year before the breach was discovered. The company said the hackers removed the malicious Sunburst code from its environment in June 2020 after delivering malicious updates to its customers since March.
Related: SolarWinds Taps Firm Started by Ex-CISA Chief Chris Krebs, Former Facebook CSO Alex Stamos
Related: Investigation Launched Into Role of JetBrains Product in SolarWinds Hack: Reports
Related: Class Action Lawsuit Filed Against SolarWinds Over Hack













