Researcher Finds Information Disclosure and Hardware Misconfiguration Flaws in ATMs Used by German Bank
German savings bank Sparkasse has started patching its ATMs and self-service terminals after a researcher discovered that the machines can be tricked into revealing a lot of sensitive information during software updates.
The issue was discovered by Benjamin Kunz-Mejri, CEO and founder of Germany-based security firm Vulnerability Lab. The researcher was using a Sparkasse terminal when the machine suddenly ejected his card, and changed its status to “temporarily not available.”
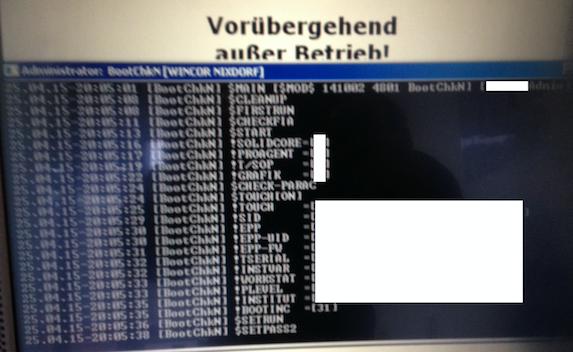
Interacting with the device caused a Windows command prompt showing details of an update process to appear on the screen. That’s when the researcher realized that the terminal had become temporarily unavailable because it was performing a software update.
Software updates are normally conducted in the background, but as Kunz-Mejri discovered, the progress and details of the update process can be made visible by interacting with the device. The researcher described his interaction with the machine as a “timing attack,” but he did not want to disclose additional details in order to prevent abuse.
When he discovered the vulnerability, Kunz-Mejri recorded a video of the information displayed on the terminal’s command prompt screen. After reviewing the recording, he determined that the update process exposed a lot of sensitive information, including the bank’s main system branch usernames, serial numbers, firewall settings, network information, device IDs, ATM settings, and two system passwords.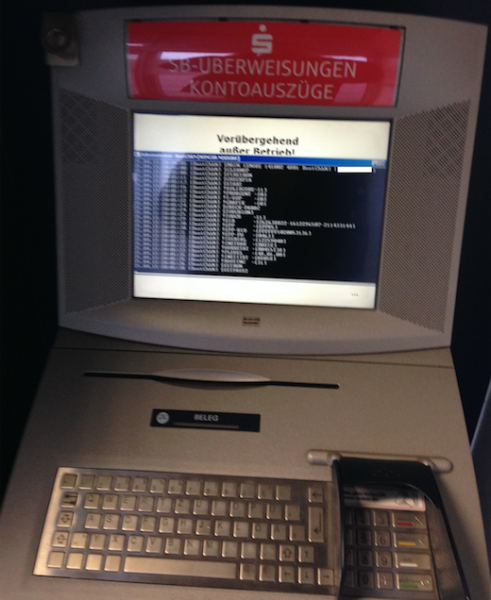
The researcher also found that the self-service terminal’s keyboard was not disabled while the update was performed. Since these devices have a full keyboard, an attacker can execute system commands via the available command prompt on the underlying Windows operating system. The expert also noted that his interaction with the machine had caused the card reader to remain available and usable for other operations.
The tested devices are manufactured by Wincor Nixdorf, a German company that manufactures, sells, installs and services retail and banking hardware and software. The affected ATMs and self-service terminals are running Windows 7 and Windows XP operating systems, Vulnerability Lab said.
In an advisory provided to SecurityWeek, Vulnerability Lab described several possible attack scenarios. In one scenario, the attacker records the information displayed on the screen during the update process and uses it to perform a man-in-the-middle (MitM) attack on the targeted bank’s local network. It’s worth noting that the attacker would require access to the local network in the bank’s building to conduct such an attack.
An attacker who can gain access to the local network can also use the exposed information to reconfigure the ATM with a rogue update that is made to look like it’s coming from the service provider’s servers, the security firm said.
Researchers also believe an attacker could conduct fraudulent transactions by tampering with the ATM in an effort to crash it and corrupt its logging or debugging mechanism.
If fraudsters can determine the time and date of update schedules, they can conduct a larger, coordinated attack targeting multiple ATMs and self-service terminals, and use the obtained information in future operations, Vulnerability Lab has warned.
According to Vulnerability Lab, it takes 17 minutes to record all the information displayed on the screen.
While only machines used by Sparkasse have been tested, the security firm believes other banks that use Wincor Nixdorf ATMs and self-service terminals might be affected as well.
Sparkasse and Wincor Nixdorf have not responded to SecurityWeek’s request for comment.
The information disclosure and hardware misconfiguration flaws were first reported to Sparkasse’s Security and Data Protection team in May, and the existence of the issues was confirmed shortly after the vulnerability report reached the bank’s Finance Security Center in Frankfurt, Vulnerability Lab said.
The organization has already rolled out updates that address the vulnerabilities to some of its ATMs in the German city of Kassel (Hessen) as part of a pilot program. The update will be installed in other regions after the new configuration is tested properly, Vulnerability Lab said.
Sparkasse has thanked Kunz-Mejri for his effort and awarded him an undisclosed amount of money, documents seen by SecurityWeek show. Kunz-Mejri says this is the first time a German bank acknowledges a security researcher for finding vulnerabilities in self-service terminals and ATMs.
Incidents involving hacked ATMs are not unheard of in Germany. Last week, Berlin Police announced that they have been looking for a man who illegally withdrew cash from two ATMs using a USB stick that he connected to the devices after unscrewing their front panel. This technique has been known for several years.
The suspect was caught on video and investigators have released a couple of photos in hopes that someone will identify him.














