The Same Platform Used to Create Stuxnet and Duqu Could have Made Other Malware That Remains Unknown. As The Platform Continues to Develop, We’re Likely to see More Modifications in the Future.
New research from Kaspersky Labs has revealed that the platform dubbed “tilded” (~d), which was used to develop Stuxnet and Duqu, has been around for years. Moreover, while they are presently unknown, the tilded platform has been used to create similar Trojans.
“The drivers from the still unknown malicious programs cannot be attributed to activity of the Stuxnet and Duqu Trojans,” said Alexander Gostev, Chief Security Expert at Kaspersky Lab. “The methods of dissemination of Stuxnet would have brought about a large number of infections with these drivers; and they can’t be attributed either to the more targeted Duqu Trojan due to the compilation date.”
“We consider that these drivers were used either in an earlier version of Duqu, or for [an] infection with completely different malicious programs, which moreover have the same platform and, it is likely, a single creator-team,” Gostev explained.
Gostev and Kaspersky’s Igor Sumenkov have put together some interesting research. The key point being the person(s) behind what the world knows as Stuxnet and Duqu, have actually been using the same development platform for several years. The platform, called tilded (~d) because of the naming convention used by the developers when creating new files, receives semi-regular updates to its code. Each update makes the Malware stronger, and trickier to catch.
 “In terms of architecture, the platform used to create Duqu and Stuxnet is the same. This is a driver file that loads a main module designed as an encrypted library. At the same time, there is a separate configuration file for the whole malicious complex and an encrypted block in the system registry that defines the location of the module being loaded and name of the process for injection,” the research explains.
“In terms of architecture, the platform used to create Duqu and Stuxnet is the same. This is a driver file that loads a main module designed as an encrypted library. At the same time, there is a separate configuration file for the whole malicious complex and an encrypted block in the system registry that defines the location of the module being loaded and name of the process for injection,” the research explains.
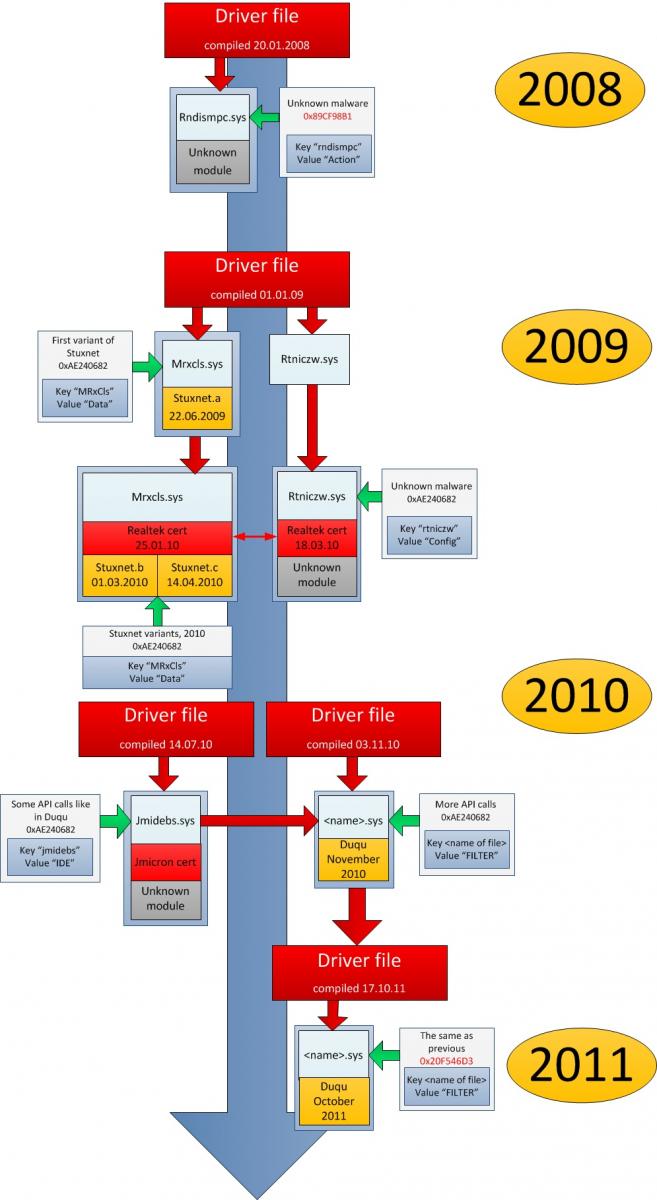 The history of Stuxnet and Duqu are established, but another interesting point in the Kaspersky research is the discovery of a previously unknown driver developed on the same ~d platform. The newly discovered variant used a stolen digital certificate from Realtek, but it was signed months after the previous Realtek certificate used by Stuxnet. Moreover, this new variant used a completely different registry key and data block. So it wasn’t Stuxnet, this was something different based on the same building blocks.
The history of Stuxnet and Duqu are established, but another interesting point in the Kaspersky research is the discovery of a previously unknown driver developed on the same ~d platform. The newly discovered variant used a stolen digital certificate from Realtek, but it was signed months after the previous Realtek certificate used by Stuxnet. Moreover, this new variant used a completely different registry key and data block. So it wasn’t Stuxnet, this was something different based on the same building blocks.
“We searched for additional information about other users who had the same file, but were unable to find anything! Moreover, we could find no information at all about the file’s name (rtniczw.sys) or its MD5 in any search engine. The file had been identified only once: it had been sent for scanning to VirusTotal from China in May 2011,” Kaspersky’s researchers reported.
If anything, it looks as if those responsible for ~d were testing the stealth of their variant. Interestingly enough, this variant was discovered by Kaspersky only because it was flagged as Stuxnet.A by their detection engines.
Adding to the evidence that the ~d platform has been in a constant state of development, was the discovery of a second previously unknown variant in the ~d family. This time, the file was discovered in Kaspersky’s Malware archive, and had been hidden there for over a year. This file had a compilation date one year older than the aforementioned unknown variant and its relative Stuxnet.A. It also had a different registry key and encryption key.
When it came to the registry data block, the previously unknown variant used ‘Config’ whereas this one used ‘Action’. For those keeping track, Stuxnet.A/B/C uses ‘Data’ – Duqu.A/B uses ‘Filter’. (Duqu drivers have unique file names for each of the variants. Their functionality, however, is identical, Kaspersky says.)
“From the data we have at our disposal, we can say with a fair degree of certainty that the ‘Tilded’ platform was created around the end of 2007 or early 2008 before undergoing its most significant changes in summer/autumn 2010. Those changes were sparked by advances in code and the need to avoid detection by antivirus solutions,” Kaspersky concluded.
“There were a number of projects involving programs based on the “Tilded” platform throughout the period 2007-2011. Stuxnet and Duqu are two of them – there could have been others, which for now remain unknown. The platform continues to develop, which can only mean one thing – we’re likely to see more modifications in the future.”
The entire research can be viewed here.
Additional Kaspersky research on Duqu was written in seven parts. Part One is here.















