It takes Russian state-sponsored hackers less than 20 minutes to start moving laterally within a targeted organization’s network after the initial breach, according to CrowdStrike’s 2019 Global Threat Report.
The security firm last year introduced a concept it named “breakout time,” which is the time it takes a threat actor to start moving laterally within a network after the first endpoint device has been compromised.
For this year’s report, which is based on data from over 30,000 intrusion attempts, the company has measured the average speed of nation state actors believed to be operating on behalf of Russia, China, North Korea and Iran. The breakout time of profit-driven cybercriminals has also been analyzed for comparison.
CrowdStrike has found that Russian state-sponsored hackers are the fastest as it only takes them roughly 18 minutes to start moving laterally after the initial breach. North Korean threat groups are the second fastest with an average breakout time of 2 hours and 20 seconds.
Chinese threat actors come in third with roughly 4 hours, followed by Iranian groups, which have an average breakout time of just over 5 hours.
Cybercriminals are the slowest with a breakout time of nearly 10 hours. However, it’s worth mentioning that this is based on data from all the groups tracked by CrowdStrike, but the company has pointed out that some individual crime groups can move much faster and they rival even the quickest nation-state actors.
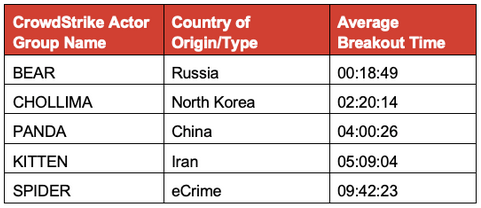
“State-sponsored adversaries out of Russia (BEARS) ranked first — almost eight times faster, on average, than their nearest competitor. While we certainly expected them to come out on top, given how effective their tradecraft usually is in comparison with other threat actors, even we were surprised by the data and how fast they can move inside a network once they get a foothold,” explained Dmitri Alperovitch, CrowdStrike co-founder and CTO.
“Another big revelation was who took the second-place ranking. North Korean-based threat actors were on average almost twice as fast as Chinese state-sponsored adversaries,” Alperovitch added. “This is likely due in part to North Korean actors having almost 20 years of experience in pursuing a very aggressive cyber offensive program. In fact, I consider them to be the most innovative threat actors in terms of their use of cyber offensive operations.”
The Chinese government has continued to target the United States, particularly with operations whose goal is to steal intellectual property, despite the pact signed by the two countries back in 2015. CrowdStrike says it has observed an “increasing operational tempo from China-based adversaries” and the company believes this tempo will accelerate during the ongoing US-China trade war.
Another interesting observation made by CrowdStrike is that threat actors believed to be operating on behalf of China, Russia and Iran have been launching campaigns aimed at the telecommunications sector.
“This trend likely supports state-sponsored espionage actors as they seek to gain access to a broad customer base that relies on telecom services,” CrowdStrike said in its report.
CrowdStrike’s investigations from 2018 also revealed that cybercrime groups have increasingly relied on tactics typically seen in targeted attacks to deliver ransomware to large organizations. The company’s researchers also noticed an increase in collaboration between sophisticated e-crime actors.
The complete 2019 CrowdStrike Global Threat Report is available in PDF format.
Related: Organizations Still Slow to Detect Breaches
Related: Software Supply Chain Increasingly Targeted in Attacks













