Most Businesses Not ‘Fully Prepared’ to Handle Data Security Incidents
There is a perception that how quickly an organization detects a security incident and executes a response plan can enhance its reputation. This potential return on investment is encouraging more organizations to focus their energies on a formal incident response team and plan, according to a survey conducted by The Economist Intelligence Unit for Arbor Networks.
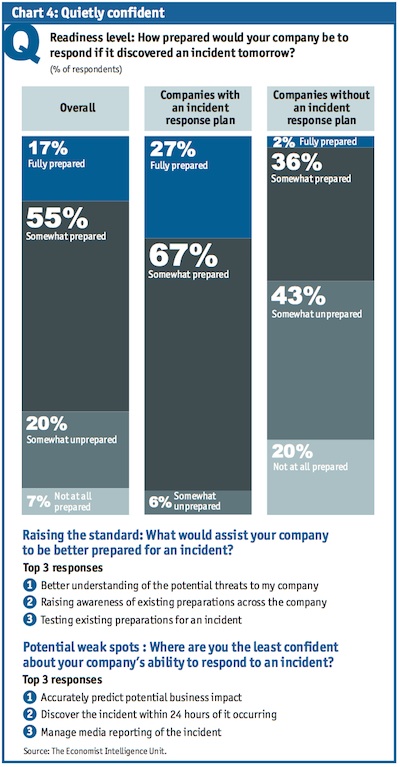
The latest survey focused on incident response plans and asked 360 business executives the question, “Are business leaders ready?” On one hand, the results appeared quite positive, with more than 60 percent of organizations reporting they have a dedicated incident response team and a defined plan in place. This number is set to rise above 80 percent in the next few years, Arbor Networks said. However, there is something still missing in their preparations, as nearly 83 percent of businesses felt they were still not “fully prepared” to handle an online security breach.
Even if the respondents did not feel they were “fully prepared,” at least 73 percent felt “somewhat prepared” for an incident, the survey found. Having a formal response plan and a dedicated team helped organizations feel a bit more prepared than not having one at all, Arabella Hallawell, vice-president of corporate strategy at Arbor Networks, told SecurityWeek. It was likely the gap between “somewhat” and “fully” would be narrower if the executives and managers in the survey had a greater understanding of potential threats, Hallawell said.
Executives struggle with predicting all possible scenarios and understanding the potential impact on business, Hallawell said.
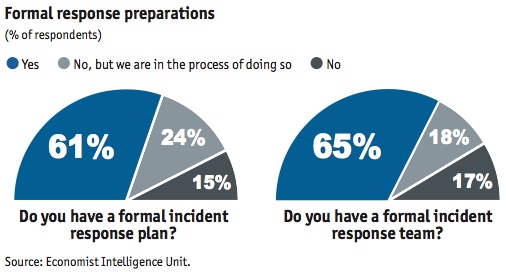
Nearly 61 percent of the respondents in the survey said they had a formal incident response plan, and 65 percent had a formal incident response team. The survey found that larger firms, those with an annual revenue of more than $500 million, are more likely to have an incident response plan than smaller businesses. Even so, these smaller businesses are catching up, as nearly 32 percent said they were in the process of defining their plans.
 Organizations had plans for specific scenarios, such as a response to data breaches, hacktivist attacks, or password loss, to name a few and close to half of the organizations in the survey had a formal method for classifying incidents. Organizations need to realize these plans have to remain flexible. “When an incident occurs, it will not fit neatly into the plan,” the report cautioned.
Organizations had plans for specific scenarios, such as a response to data breaches, hacktivist attacks, or password loss, to name a few and close to half of the organizations in the survey had a formal method for classifying incidents. Organizations need to realize these plans have to remain flexible. “When an incident occurs, it will not fit neatly into the plan,” the report cautioned.
One of the key takeaways from this report is that just having an incident response plan and team wasn’t enough. In fact, 41 percent of respondents said a better understanding of potential threats would help them be better prepared. The problem lay in the fact that executives could not be sure everything had been taken into account, Hallawell said.
About half of the respondents felt they were unable to predict the business impact of a breach before the actual incident and a little over a third, or 36 percent of executives, were not confident their security teams would be able to identify a breach within 24 hours of it happening, the survey found. More importantly, half of the organizations in the survey felt they couldn’t predict beforehand the impact a security incident would have on the business.
Organizations need to develop “a response capability,” the report recommended, where the right people are identified beforehand who could react to a given situation and respond accordingly.
For the majority of the organizations in the survey, the most common incidents were not malicious, but rather, mistakes, the report found. In fact, three-quarters of the respondents, or 75 percent, said their organization had suffered a security incident at least once over the past two years, of which accidental major systems outages accounted for 29 percent of the incidents, and an employee misplacing sensitive data was 27 percent. Organizations should not be focusing only one set of potential threats, but be prepared to handle threats from both external and internal actors, the report suggested.
“A company is more likely to lose control of sensitive data through the actions of an employee than as a result of theft by an external actor,” Arbor’s Hallawell said.
The survey examined how confident senior managers were that their organizations would be able to handle a security breach and the kinds of response plans the organizations had—or did not have—in place. Arbor Networks worked with the Economist Intelligence Unit to survey 360 senior business leaders around the world. More than 70 percent of the respondents were C-level managers or board members, according to Arbor Networks. Roughly one third of the respondents were based in North America, one third in Europe, and one third in Asia Pacific.
While government, information technology, and the oil-and-gas industries account for the majority of online incidents globally, energy and natural resources, and media and entertainment sectors all saw “above average increases” in the number of incidents, Arbor Networks found. While government, IT, and oil-and-gas are increasingly becoming harder to compromise, criminals are looking elsewhere for weak spots to break in.
Nearly two-thirds of the respondents said being able to respond to an incident effectively is “an opportunity to enhance the reputation of their organization,” the report found. Being prepared is “now of the utmost importance,” the report concluded.
The full report is available online in PDF format.
Related Reading: Preparing for the Inevitable Data Breach: Discussion
Related Reading: What Happens to Stolen Data After a Breach?
Related Reading: Technical, Management Challenges Facing Incident Response
Related Reading: Strategic Incident Response: The Art of Choreographed Reaction
Related Reading: Security Incident Response Teams Getting Short End of Budget Stick












