A team of researchers from Virginia Tech, the University of Electronic Science and Technology of China, and Microsoft Research has discovered a new and stealthy GPS spoofing method that has been proven to be highly effective against road navigation systems.
GPS spoofing has been around for many years. This attack method can in theory be used to trick drivers into going to an arbitrary location, but in practice the instructions provided by the targeted navigation system often contradict the physical road (e.g. make a left turn on a highway), making it less likely to work in a real-world scenario.
Researchers now claim to have discovered a more efficient method that is less likely to raise suspicion. Using this technique an attacker could trick the victim into following an incorrect route (e.g. cause ambulances and police cars to enter a loop route), deviate a targeted vehicle to a specific location, or cause the target to enter a dangerous situation (e.g. enter a highway the wrong way).
For the attack to work, the attacker needs to know the target’s approximate destination and the most likely victim of this technique would be an individual who in not familiar with the area.
Using 600 real-world taxi routes from Manhattan and Boston, the researchers have created an algorithm that generates a virtual route mimicking the shape of real roads. The attack is most likely to work in a city where road networks are dense.
The attacker creates false GPS signals in an effort to set the final location to a nearby “ghost location.” The navigation system recalculates the new route, which researchers have dubbed the “ghost route,” and guides the victim, turn-by-turn, to the ghost location.
In order to avoid raising suspicion, the ghost route is generated based on the collected taxi trips. The search algorithm is run at each road segment in an effort to identify all possible attack (ghost) locations. During tests, the algorithm identified, on average, roughly 1,500 potential attack routes for each trip.
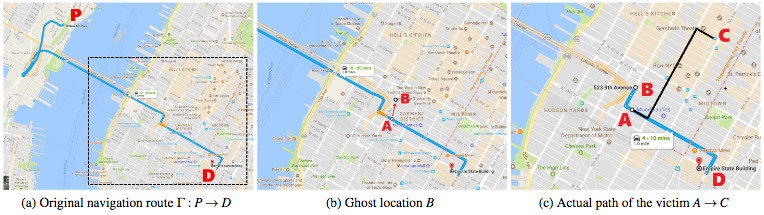
“The algorithm crafts the GPS inputs to the target device such that the triggered navigation instruction and displayed routes on the map remain consistent with the physical road network,” researchers said in their paper.
In some cases, if the original location is not on the route to the ghost location, the user may be informed by the navigation system that the route is being recalculated, but researchers have determined based on a survey that it might not raise too much suspicion considering that this can often occur in a real-world scenario.
These types of attacks can be carried out using a portable GPS spoofer, which costs roughly $200, from a distance of 40-50 meters (130-160 feet). The attacker can either follow the targeted vehicle or place the spoofer inside or under the targeted car and control it remotely.
The researchers reproduced the attack in a real-world scenario using their own car, which they drove after midnight in suburban areas to avoid causing any problems. They also asked 40 individuals (20 in the U.S. and 20 in China) to use a driving test simulator that was attacked via the newly discovered method. The attack’s success rate was 95%, with only one Chinese and one U.S. participant detecting the attack.
Related: Hackers Can Hijack, Sink Ships
Related: Many GPS Tracking Services Expose User Location, Other Data














