Symantec researchers report a massive increase in the amount of boot time malware striking users
In the August 2011 Symantec Intelligence Report, the company noted there have already been as many new boot time malware threats detected in the first seven months of 2011 as there were in the previous three years. Also known as MBR (master boot record) threats, the malware infects an area of the hard disk that makes them one of the first things to be read and executed when a computer is turned on. This enables the threats to effectively dodge many security defenses.
In June, Microsoft warned Windows users about a bootkit Trojan known as Popureb, touching off discussions about whether or not infected users were better off completely re-installing Windows.
“MBR infections offer great scope for deep infection and control of computers, which makes the idea attractive to malware creators,” said Paul Wood, senior intelligence analyst, Symantec.cloud, in a statement. “Contemporary MBR infection methods are a fairly complex affair usually executed by highly skilled individuals.”
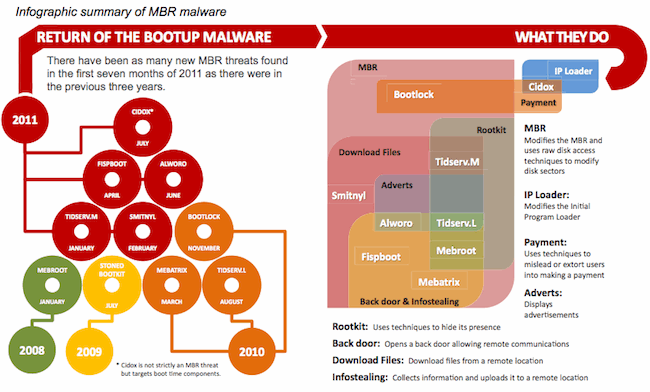
Infecting the MBR is not a new technique per se; many of the old boot sector viruses from over a decade ago did something similar, the report notes. The difference is modern MBR malware do so much more than just infecting the MBR. It certainly looks as if MBR malware is making a comeback in 2011.
The report also noted some other movement in the malware world. According to Symantec, the most frequently blocked malware for the past month was W32.Ramnit!html, a generic detection for .HTML files infected by W32.Ramnit(1). Ramnit spreads through removable drives and by infecting executable files such as .DLL, .EXE and .HTM extensions. Variants of the worm accounted for 15.8 percent of all malicious software blocked by Symantec endpoint protection technology in August.
While the overall ratio of spam in global email traffic dropped 1.9 percentage points to 75.9 percent between July and August, the ratio of email-borne viruses increased .14 percent. According to the report, spammers are still using to a tried-and-true operation known as a “pump-and-dump” stock scam. Such scams, Symantec explained, can artificially drive up the price of stock to allow the scammers to sell their shares for high profits.
“Scammers can make substantial profits in a matter of days with a well-executed pump-and-dump spam,” Wood said. “In the current turbulent environment many people may be convinced to invest in stocks that the scammers claim will benefit from the market turbulence.”
The full August 2011 Symantec Intelligence Report is available here.
Suggested Reading: Attacks on Mobile and Embedded Systems: Current Trends
Suggested Reading: Vulnerability Management Buyer’s Checklist: Key Questions to Ask
















