Wi-Fi enabled LED light bulbs manufactured by LIFX have been hacked by researchers from Context Information Security, the company said Friday.
The energy efficient light bulbs are designed to use a Wi-Fi connection to allow users to control them through a smartphone application. As part of its effort to raise awareness of Internet of Things (IoT) security, Context demonstrated that the lack of protection measures enables an attacker within the wireless range to control all connected bulbs and expose user network configurations such as Wi-Fi credentials.
According to Context, there are three main communication components: bulb Wi-Fi communication, smartphone to bulb communication, and bulb mesh network communication. The system is designed so that only a master bulb is connected to the Wi-Fi network through which it receives commands from the smartphone. The other bulbs get the commands from the master bulb over an 802.15.4 6LoWPAN wireless mesh network. When a new bulb is added, it receives the Wi-Fi details, information which is encrypted, from the master bulb.
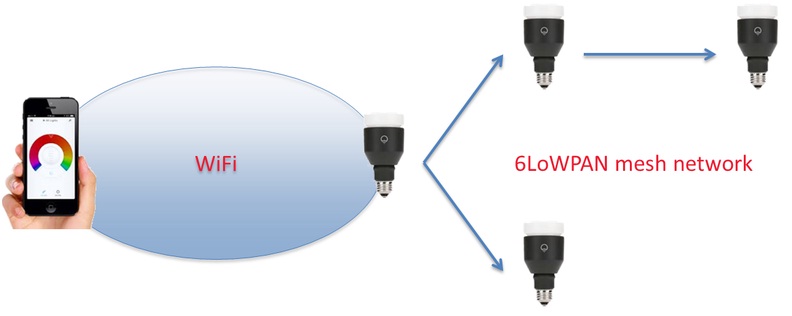
The first security issue found by researchers was the fact that the wireless communication protocols used for the bulb mesh network were in most part unencrypted, allowing them to inject traffic and control the light bulbs with the aid of an AMTEL AVR Raven wireless kit. By injecting arbitrary packets into the mesh network, an attacker can request Wi-Fi credentials, but the information is encrypted, Context said. Experts found a way to decrypt the information by extracting the firmware from the device and reverse engineering it.
“Armed with knowledge of the encryption algorithm, key, initialization vector and an understanding of the mesh network protocol we could then inject packets into the mesh network, capture the WiFi details and decrypt the credentials, all without any prior authentication or alerting of our presence,” Context researchers explained in a blog post.
Context reported its findings to LIFX, which released a firmware update (version 1.2) to address the security issues. In the latest version of the firmware, 6LoWPAN traffic is encrypted and adding new bulbs to the network is done in a secure manner. Representatives from the manufacturer claim there is no evidence that the vulnerability has been exposed by anyone besides Context, most likely due to the complexity of the attack.
“Hacking into the light bulb was certainly not trivial but would be within the capabilities of experienced cyber criminals,” said Michael Jordon, research director at Context Information Security. “In some cases, these vulnerabilities can be overcome relatively quickly and easily as demonstrated by working with the LIFX developers. In other cases the vulnerabilities are fundamental to the design of the products. What is important is that these measures are built into all IoT devices from the start and if vulnerabilities are discovered, which seems to be the case with many IoT companies, they are fixed promptly before users are affected.”














