The existence of a vulnerability in a portal used internally by PayPal staff was recently disclosed by Germany-based security research company Vulnerability Lab.
The security hole plagued an “Ethernet portal” used by PayPal employees to review user data in a secure way, Benjamin Kunz Mejri, the founder and CEO of Vulnerability Lab, told SecurityWeek. The expert managed to inject code into his own user profile, which got executed when someone from PayPal visited the profile.
“An application-side validation Web vulnerability and a filter bypass has been discovered in the official PayPal Inc. Ethernet portal backend application (API). The filter bypass allows remote attackers to evade the regular parse and encode filter mechanism of the PayPal online-service portal Web-application. The persistent input validation vulnerability allows remote attackers to inject own malicious script codes on the application-side of the vulnerable service,” reads the advisory provided by Vulnerability Lab to SecurityWeek.
“In the attack scenario we injected malicious test codes with scripts in the most attractive values of the PayPal user profile database ̶ `bank account owner/holder (cardholder)`, `name/surname`, `company name` and of course the `account owner`,” the researchers explained.
The flaw, which has been catalogued by the security firm as being critical, could have been exploited remotely by using a low-privilege PayPal account, and did not require any interaction from the victim. Attackers could have leveraged the security issue to hijack user sessions, gain access to the accounts database, compromise developer and administrator accounts, perform external redirects, and for persistent manipulation of affected or connected modules, Vulnerability Lab said.
The vulnerability, for which researchers received a $1,000 reward, was reported to the payment processor in February 2013 and it took the company around 10 months to address the issue. Vulnerability Lab got permission to disclose the existence of the flaw only on July 4, Kunz Mejri said.
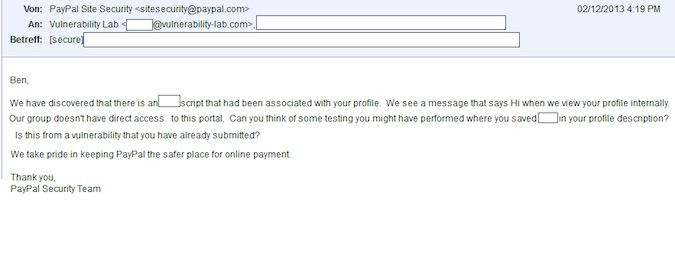
Interestingly, just before the details of the bug were disclosed to PayPal, the company’s security team contacted Kunz Mejri after noticing that whenever they accessed his security researcher profile they were presented with a message that read “Hi.”
A proof of concept and the technical details for this vulnerability are available online.














