A group of security and privacy researchers from the Institute of Media Informatics at Ulm University in Germany, is claiming to have discovered a serious security vulnerability in Google’s ClientLogin protocol.
In a recent analysis of the Android platform, the group discovered that when Android users are connected to an unencrypted open Wifi network, an attacker could both read transmitted synchronization data of Google Contacts, Calendar and Picasa Web Albums, and capture the authToken that’s user for authentication.
Bastian Könings, one of the researchers from the group, told SecurityWeek, “The adversary could use this authToken to gain full access to the data API of the specific service and view, modify or delete any contacts, calendar events, and web albums of that user.”
“The vulnerability isn’t limited to Android Google apps, but to any apps and desktop applications that use Google’s ClientLogin protocol over HTTP rather than HTTPS,” Könings added.
The group notes an interesting scenario, saying that beyond the stealing user information, an adversary could perform subtle changes without the user noticing. “For example, an adversary could change the stored email address of the victim’s boss or business partners hoping to receive sensitive or confidential material pertaining to their business,” the group noted in a post disclosing the vulnerability. “Due to the long lifetime of authTokens, the adversary can comfortably capture a large number of tokens and make use of them later on from a different location,” the group added.
This type of attack is similar in scope to stealing Web site session cookies, sometimes called “session hijacking” or “Sidejacking. Sidejacking caught much attention surrounding the released of Firesheep, a plugin which enabled drag and drop hacking attacks against sites such as Facebook, Twitter, Yahoo! and more.
Bastian Könings told SecurityWeek via email that the group has contacted Google about this issue and that it was fixed for Calendar and Contacts in Android 2.3.4. However, Könings said that Picasa sync of the stock Gallery app still remains vulnerable. “Unfortunately, the distribution of Android 2.3.4 is rare and most Android versions are 2.3.3 and below,” he added.
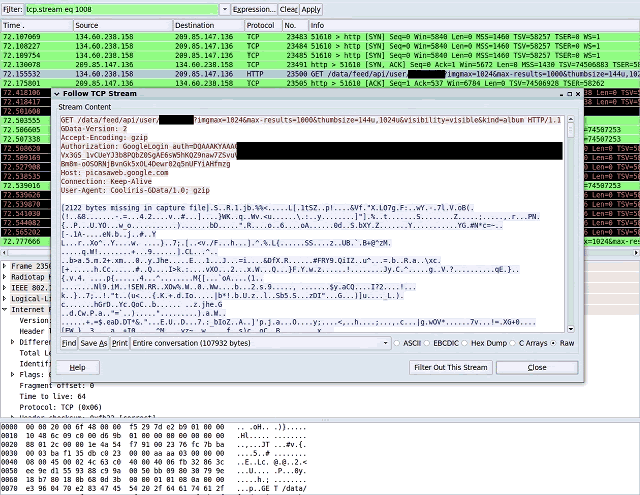
More details from the discovery are available here. The Wireshark screenshot below shows the authToken for ClientLogin in a data API request to the Picasa Web Albums service.