A survey of more than 300 ethical hackers conducted by cybersecurity companies Bishop Fox and SANS Institute found that many could execute an end-to-end attack in less than a day.
The respondents were mostly from the United States, but they represented organizations that have operations around the world. A vast majority of them have been conducting ethical hacking for 10 years or less. Their experience includes being a member of an organization’s internal security team, offensive security firm consulting, bug bounty hunting, and independent hacking-for-hire.
The goal of the survey is to gain insight into how attackers think, how fast they are, and the tools they use, as well as to obtain information that could be useful to defenders looking to improve their security posture and refine their defensive and offensive strategies.
Nearly 40% of the surveyed ethical hackers said they can break into an environment more often than not, if not always.
When asked about how long it takes them to discover an exploitable vulnerability that gives them access to a targeted organization’s environment (perimeter breach), roughly 40% of respondents indicated that it takes them five hours or less, and nearly 5% believe they can do it in less than an hour.
Once they have found the exposure, more than 58% said they could break into the targeted environment in five hours or less.
When it comes to attack surface, the most commonly identified exposures involve vulnerable configurations, exposed web services, and vulnerable software.
After gaining initial access into an organization, well over half of respondents said it takes them five hours or less to access the targeted data or system through privilege escalation or lateral movement. Nearly 64% can collect and exfiltrate data within a five-hour window, with 16% claiming they could do it in less than an hour.
When asked about how long it takes them to conduct an end-to-end attack, 18% said they could do it in 10 hours or less, and more than half believe they could do it within a day.
The ethical hackers who took part in the survey were also asked about successfully pivoting to a new attack method if their initial vector fails. Only 38% said they had a high success rate at changing attack methods, with the survey showing that the more experience a hacker has the more likely they are to succeed.
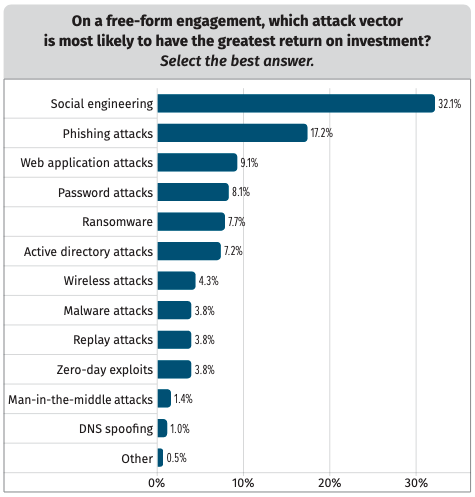
As for the attack vectors that are most likely to have the greatest return on investment, one-third of respondents named social engineering, followed by phishing.
Nearly 60% said they use open source tools in free-form engagements, and only 11% rely on commercial tools.
Many respondents believe organizations don’t have the detection and response capabilities required to identify and stop an attack.
The complete report, titled ‘Think Like a Hacker: Inside the Minds and Methods of Modern Adversaries’ is available in PDF format.
Related: Ransomware Often Hits Industrial Systems, With Significant Impact














