Public advisories describing vulnerabilities in industrial control systems (ICS) often fail to convey the true impact of the flaws, according to a report published today by ICS cybersecurity firm Dragos.
An analysis of 163 advisories published last year by ICS-CERT and others – excluding reports on medical device flaws, which ICS-CERT regularly covers – allowed Dragos to compile some useful statistics.
The company determined that patches for nearly two-thirds of the security holes disclosed last year don’t fully eliminate the risk due to the fact that the affected systems had been insecure by design.
Another interesting point made by Dragos in its report is that 85% of the vulnerabilities can be exploited late in the kill chain and they are not useful for getting an initial foothold in the targeted organization’s network. This means that an attacker who manages to exploit the flaws has had access to the target’s network for some time.
Once exploited, one-third of the vulnerabilities lead to what Dragos describes as “loss of view,” which results in the victim not being able to monitor or read the state of the compromised system.
In 29% of cases, exploitation of the bugs leads to “loss of control,” preventing any modifications to the state of the system. In roughly the same percentage of cases, exploitation of a flaw leads to both loss of control and loss of view.
“Vulnerabilities which lead to both a loss of view and control occur in the core of traditional control networks affecting both field devices (PLCs, RTUs, etc.) as well as management such as human-machine interface (HMI) systems and engineering workstation (EWS) software,” Dragos explained in its report. “This means that a large percentage (61%) of ICS-related vulnerabilities will cause severe operational impact if exploited.”
Learn More at SecurityWeek’s ICS Cyber Security Conference
Many of the flaws covered by the advisories analyzed by Dragos affect products that are further away from the perimeter of the operational technology (OT) network, which makes them less likely to be exploited.
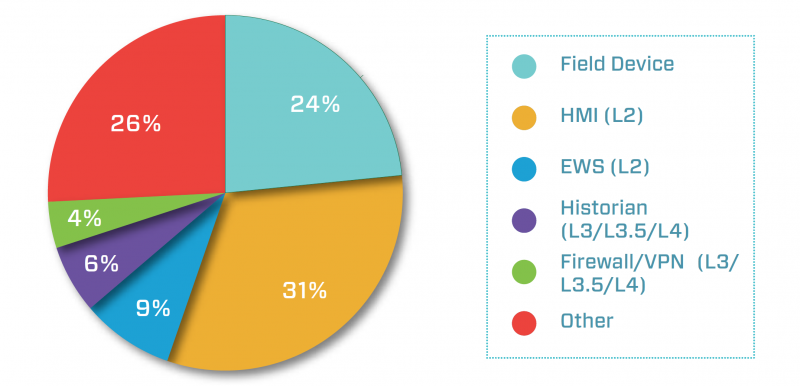
However, 15% of advisories describe vulnerabilities in components located very close to the network perimeter. Systems such as historians, OPC servers, firewalls, VPN products, and cellular gateways are often directly accessible from the business network and even from the Internet, which makes them more likely to be attacked.
Nearly one-quarter of the weaknesses impact field devices, while 31% affect HMIs.
“Most of the control system vulnerability patching focus should be placed on the 30% of vulnerabilities which impact exterior-facing systems,” Dragos said. “Since so many assets and interior control elements are nowhere near a network border, applying patches in the 85% of interior and none-to-medium proximity cases would likely have little to no reduction in risk for impact against attack.”
Dragos also busted a common myth claiming that most ICS vulnerabilities are found in demo or free software rather than actual control systems. However, the company found that 63% of all ICS-related flaws disclosed last year impacted software or hardware that could not have been obtained for free.
The security firm’s analysis also revealed that 72% of public advisories describing ICS flaws did not provide any alternative mitigations. According to Dragos, recommending the use of VPNs and trusted networks, which is included in most advisories, does not count as alternative mitigations.
Related: Non-Targeted Malware Hits 3,000 Industrial Sites a Year
Related: Increasing Number of Industrial Systems Accessible From Web
Related: One-Third of Industrial Networks Connected to Internet














