An investigation conducted by industrial cybersecurity firm Dragos into the recent cyberattack on the water treatment plant in Oldsmar, Florida, led to the discovery of a watering hole attack that initially appeared to be aimed at water utilities.
Law enforcement revealed in early February that a hacker had gained remote access to systems at the water plant in Oldsmar and attempted to elevate levels of a certain chemical to a point where it could put the public at risk of being poisoned.
The attacker abused TeamViewer, which staff at the plant had been using to monitor and control systems remotely. Due to password sharing and other poor security practices, it was easy for the hacker to gain access and start making unauthorized changes in an HMI. Fortunately, the breach was spotted — staff noticed the mouse moving on the screen — and a disaster was prevented.
While investigating the incident, Dragos’ threat hunters noticed that the website of a Florida water infrastructure construction company had been compromised and set up to serve as a watering hole. Malicious code planted on this site collected information on the computers used to access it.
The malicious script was present for nearly two months between December 2020 and February 2021, and it collected information about the operating system, CPU, browser, input methods, camera, accelerometer, microphone, touchpoints, video card, time zone, geolocation, the screen, and browser plugins. In addition, it directed victims to a couple of sites that collected browser cipher fingerprints, which are used by some network defense solutions to detect connections from hosts infected with malware.
Dragos determined that more than 1,000 computers accessed the watering hole during the two-month timeframe, including state and local government organizations, municipal water utility customers, and private firms related to the water industry. Most of the organizations profiled by the malicious code were in Florida and other parts of the United States. This appeared to indicate that the watering hole was set up as part of a targeted attack aimed at the water sector in the U.S.
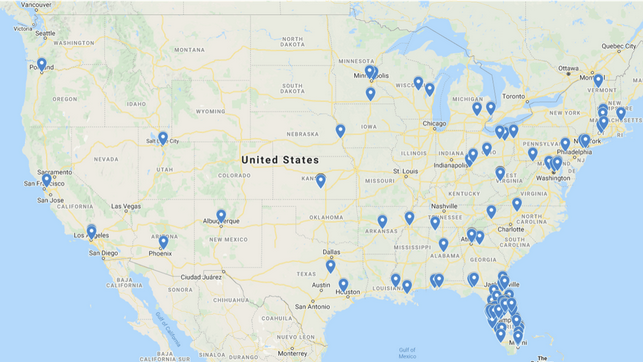
Interestingly, just hours before the Oldsmar water plant was hacked, someone from the facility also accessed the watering hole. However, this does not appear to be related to the highly publicized hack. In fact, Dragos said it had “medium confidence” that no organization was compromised through the watering hole attack.
An analysis of the code used in the watering hole attack led investigators to a cybercrime website named DarkTeam Store, which had a section that computers infected with a piece of malware named Tofsee — specifically a variant tracked by Dragos as Tesseract — would connect to.
“With the forensic information we collected so far, Dragos’ best assessment is that an actor deployed the watering hole on the water infrastructure construction company site to collect legitimate browser data for the purpose of improving the botnet malware’s ability to impersonate legitimate web browser activity,” Dragos said in a blog post.
The company also noted, “We do not understand why the adversary chose this specific Florida water construction company site to compromise and to host their code. Interestingly, and unlike other watering hole attacks, the code did not deliver exploits or attempt to achieve access to victim computers. It is possible the actor believed that the water infrastructure construction website would allow more dwell time to collect data important for the actor’s objectives, than perhaps a busier but more closely monitored website with a dedicated security team.”
Dragos pointed out that even though the watering hole attack did not appear to be directly aimed at the water industry, the incident does highlight the importance of controlling access to untrusted sites, particularly in the case of OT and ICS environments.
Related: Small Kansas Water Utility System Hacking Highlights Risks
Related: U.S. Gov Warning on Water Supply Hack: Get Rid of Windows 7
Related: Industry Reactions to U.S. Water Plant Hack: Feedback Friday
Related: Hack Exposes Vulnerability of Cash-Strapped US Water Plants













