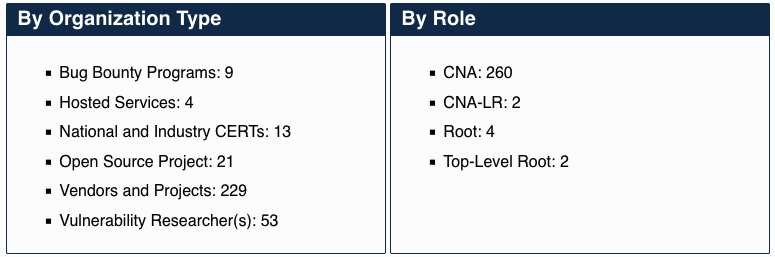
More than 50 organizations have been added as a CVE Numbering Authority (CNA) in 2022, bringing the total to 260 CNAs across 35 countries.
Most CNAs can assign CVE identifiers to vulnerabilities found in their own products, but some can also assign CVEs to flaws found by their researchers in third-party software that is not in another CNA’s scope.
 SecurityWeek has conducted an analysis of announcements made by the CVE Program and found that 54 CNAs were added in 2022, compared to 43 in 2021.
SecurityWeek has conducted an analysis of announcements made by the CVE Program and found that 54 CNAs were added in 2022, compared to 43 in 2021.
The 2022 list includes cybersecurity companies such as Proofpoint, Bugcrowd, Qualys, CyberArk, Green Rocket Security, Dragos, SailPoint, Senhasegura, NetRise, HYPR, and Netskope.
Major tech companies such as Baidu, Canon, Google (open source software), Seagate, Unisoc, GE Healthcare, Philips, Medtronic, Baxter Healthcare, and Citrix are now also CNAs.
Major industrial solutions providers such as General Electric (Gas Power), Honeywell, and Rockwell Automation can now also assign CVEs to vulnerabilities.
There are also some national organizations and nonprofits that have joined the list of CNAs, including the Dutch Institute for Vulnerability Disclosure (DIVD), Automotive Security Research Group, Slovakia’s National Cyber Security Centre (SK-CERT), and the National Cyber Security Centre in the Netherlands (NCSC-NL).
The list of new CNAs also includes Docker, WolfSSL, Grafana Labs, Honor, Zowe, OneKey, KrakenD, Dual Vipers, Baicells, HashiCorp, OpenCloudOS, OpenNMS Group, Crestron Electronics, OpenHarmony, Full Services, KNIME, OpenGauss Community, Hitachi and Hitachi Vantara, Hallo Welt, OpenAnolis, ZUSO Advanced Research Team, Go Project, JetBrains, The Missing Link Australia (TML), and the OpenBMC Project.
Related: Moussouris: U.S. Should Resist Urge to Match China Vuln Reporting Mandate
Related: Over 28,000 Vulnerabilities Disclosed in 2021
Related: Microsoft: China Flaw Disclosure Law Part of Zero-Day Exploit Surge
Related: GitHub Introduces Private Vulnerability Reporting for Public Repositories












