Organizations are getting better at detecting intrusions on their own, but it still takes them a long time to do it, according to a new report published on Tuesday by endpoint security firm CrowdStrike.
According to the 2018 CrowdStrike Services Cyber Intrusion Casebook, which is based on the analysis of over 200 major security incidents, 75% of organizations that used CrowdStrike’s incident response services in 2018 managed to internally detect a breach, up from 68% in the previous year.
However, the average attack dwell time – or the time it takes to detect an attack – was 85 days, comparable to the 86 days reported by the company in its 2017 report.
“Clearly, there is considerable room for improvement. Boards of directors, executive management, and the public at large are all rightly concerned that organizations take days, weeks or even months to detect attacks,” CrowdStrike said in its latest report.
CrowdStrike believes organizations should be able to detect a threat within one minute, investigate it in ten minutes, and remediate it within 60 minutes – the company calls this the 1-10-60 rule.
As for attack objectives, CrowdStrike says nearly half of the incidents analyzed by its experts were financially motivated. The second most common attack objective was intellectual property theft (30%), followed by theft of personal information (10%), ransomware (7%), cryptocurrency mining (3%), destruction (2%), and corporate espionage (1%).
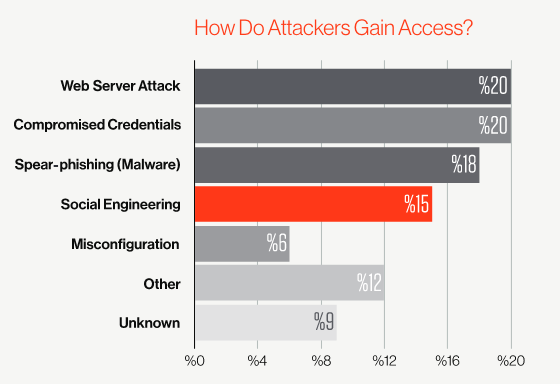
Social engineering, phishing and spear-phishing were the attack vector in roughly one-third of cases, up from 11% in the previous year. The biggest single vector remains web server attacks, accounting for nearly 20% of the total.
CrowdStrike has highlighted several important attack trends. The company says malicious actors have continued to come up with creative tactics and techniques. For example, experts uncovered cases where the attackers had been using remote access tools that provided them the ability not only to read their victims’ emails, but also to watch the email being written and sent in real time.
The company’s investigations also included cases where adversaries re-entered an organization’s network shortly after another vendor’s incident response team had been called in by the victim, and even cases where the attacker was still present on the network even after an incident response team believed that the threat was removed.
Another major problem highlighted by CrowdStrike is that attackers continue to masquerade as legitimate users. State-sponsored actors often rely on stolen credentials for email and VPN access, while profit-driven cybercriminals use credential stuffing and business email compromise (BEC) tactics.
“Today, it’s absolutely critical that cyber defenders and executives stay informed of emerging attack techniques, trends in targeting, and lessons learned from real-world cybersecurity cases,” Thomas Etheridge, VP of CrowdStrike Services, told SecurityWeek.
“In addition to detailing an uptick in social engineering, phishing and business email compromise attacks, we also established that many adversaries use commodity malware to launch destructive attacks and continue to leverage living-off-the-land techniques to stay undetected. To combat these challenges, CrowdStrike continues to advocate for faster and more effective detection and response, including the 1-10-60 rule that helps businesses lay the essential groundwork to defeat adversaries. The Services Casebook can be used as a critical guide for Corporate Boards and C-suites looking to safeguard their most valuable data,” Etheridge added.
Related: ‘Five Eyes’ Agencies Release Joint Report on Hacking Tools
Related: 92% of External Web Apps Have Exploitable Security Flaws or Weaknesses
Related: Cyberattacks Against Energy Sector Are Higher Than Average













