Less than a year after its previous release, Oracle today announced a new release of Oracle Database Firewall, the database giant’s solution to improve enterprise database security and help enterprises prevent internal and external attacks from reaching their databases.
 The latest edition of Oracle Database Firewall introduces support for MySQL Enterprise Edition, adding to previous support for Oracle Database 11g and earlier releases, IBM DB2 Linux Unix Windows, Microsoft SQL Server, Sybase Adaptive Server Enterprise (ASE) and Sybase SQL Anywhere.
The latest edition of Oracle Database Firewall introduces support for MySQL Enterprise Edition, adding to previous support for Oracle Database 11g and earlier releases, IBM DB2 Linux Unix Windows, Microsoft SQL Server, Sybase Adaptive Server Enterprise (ASE) and Sybase SQL Anywhere.
This new release also brings new reporting capabilities, including reports that help organizations more efficiently address regulatory compliance.
So how does the Database Firewall work? To address database threats, Oracle Database Firewall establishes a defensive perimeter around databases, while monitoring and enforcing regular application behavior.
“Oracle Database Firewall examines SQL traffic, creating a specific perimeter around databases,” explained Martin Kuppinger, Founder and Principal Analyst, KuppingerCole. “Based on its grammar-based analytical approach and a well thought out and efficiently manageable policy approach, organizations can relatively quickly implement Oracle Database Firewall while minimizing the risk of disruption to database applications.”
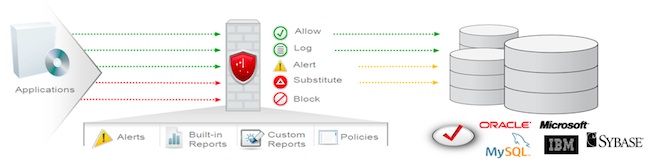
SQL Injection or “SQLi” attacks, are a common technique used by attackers that exploit a Web application vulnerability in order to access and extract data from a database. According to a 2011 Web Application Attack Report from Imperva, SQLi attacks represented of 23% of all overall attacks.
Despite the fact that SQL Injection attacks are so prevalent, and by no means new, organizations are still surprisingly vulnerable. In fact, according to a recent Independent Oracle Users Group survey, only 36 percent of respondents said that they have taken steps to ensure their applications are not susceptible to SQL injection attacks.
With protection being extended to MySQL databases, Oracle Database Firewall can help protect against data breaches without requiring any changes to existing applications, database infrastructure, or the operating system of the target database.
Oracle inherited MySQL as part of its acquisition of Sun Microsystems in a deal that closed in January 2010. Sun originally acquired MySQL AB, the open source developer of MySQL, for approximately $1 billion in 2008.
“Since most customers are at risk of SQL injection attacks, the Oracle Database Firewall provides much needed security,” said Andy Flower, President of the Independent Oracle User Group. “Oracle Database Firewall is an example of the necessary first line of defense for large and small customers that can monitor database activity and block threats before they even reach the database.
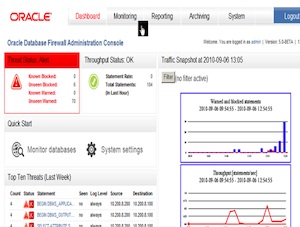 To enhance reporting capabilities, Oracle Database Firewall introduces a new reporting infrastructure for running and modifying the layout of existing reports. For customers that use Oracle Business Intelligence Publisher, they can take advantage of all capabilities offered for authoring, managing, and delivering highly formatted documents that can be designed using familiar desktop products, the company said.
To enhance reporting capabilities, Oracle Database Firewall introduces a new reporting infrastructure for running and modifying the layout of existing reports. For customers that use Oracle Business Intelligence Publisher, they can take advantage of all capabilities offered for authoring, managing, and delivering highly formatted documents that can be designed using familiar desktop products, the company said.
The new release introduces 10 new out-of-the-box reports to further help organizations comply with privacy and regulatory mandates such as Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry (PCI) Data Security Standard (DSS) and Sarbanes-Oxley (SOX).
In addition, the new release of the Oracle Database Firewall offers a new “proxy operating mode” that brings increased flexibility in deploying it on the network. New ‘multi-core’ management capabilities offer administrators fine-grained control over the resources allocated to protect specific databases for even greater scalability, Oracle said.
In an effort to help customers adopt a “defense-in-depth strategy”, Oracle Database Firewall is now also integrated with Oracle Advanced Security allowing encrypted traffic to Oracle Databases to be monitored for potential threats.
Oracle Database Firewall complements Oracle Advanced Security, Oracle Audit Vault and Oracle Database Vault.















