
A team of researchers from Japan-based cybersecurity firm Trend Micro has analyzed the communication mechanisms used by cranes and other industrial machines and discovered serious vulnerabilities that can make it easy for malicious actors to launch remote attacks.
Cranes, hoists, drills and other heavy machinery used in the manufacturing, construction, transportation and mining sectors often rely on radio frequency (RF) controllers. These systems include a transmitter that sends out commands via radio waves, and a receiver that interprets those commands.
Trend Micro researchers have conducted an in-depth analysis of these systems and found serious vulnerabilities that can be exploited for various types of attacks. They have conducted experiments in both a lab environment and in the real world to demonstrate the risks posed by these security holes.
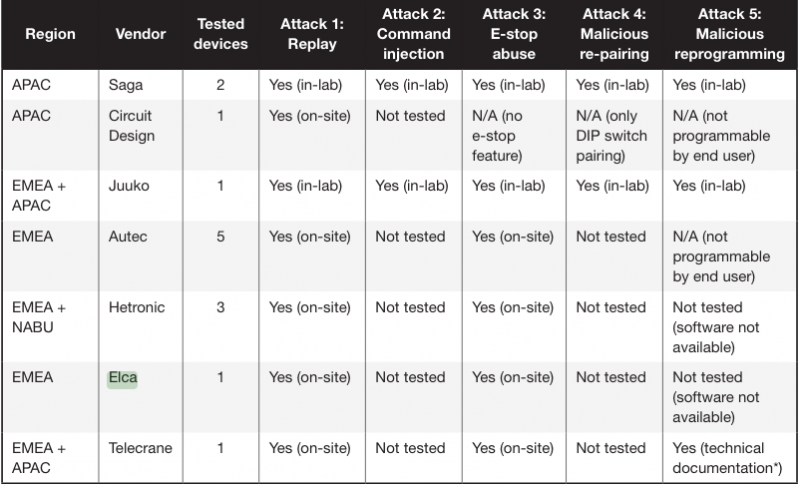
Researchers have tested products from several vendors, including Saga, Juuko, Telecrane, Hetronic, Circuit Design, Autec, and Elca, and they were all found to be vulnerable. Their tests have been conducted in 14 different real-world locations and they were also all found to be impacted.
Trend Micro has notified affected vendors of the vulnerabilities and some of them have already started taking action. ICS-CERT has published two advisories for flaws uncovered by the researchers in Telecrane and Hetronic products.
Learn More About Controller Flaws at SecurityWeek’s 2019 ICS Cyber Security Conference
The main problem found by experts is that vendors have failed to protect communications between the transmitter and the receiver, allowing attackers to capture traffic and spoof commands.
Five types of attacks have been detailed by the researchers. One of them, which is easy to carry out, involves replay attacks. In these attacks, the hacker captures a valid transmission and replays it for malicious purposes.
Command injection attacks can be even more dangerous as they allow the attacker to modify the captured RF packets before sending them to the receiver, which enables them to take complete control of the targeted machine.
One variant of the replay attack involves repeatedly sending the “emergency stop” command to the targeted crane, causing it to enter a persistent denial-of-service (DoS) condition.
Researchers warn that attackers with intermediate skills can clone the remote controller, pair the malicious controller with the crane, and unpair the legitimate controller, thus hijacking the machine.
The last type of attack detailed by Trend Micro requires more skills and knowledge. It involves the attacker trojanizing the firmware running on the controller to gain full and persistent control.
While one might think that conducting such attacks requires the hacker to be in proximity of the targeted crane, experts have demonstrated that a small, battery-powered device planted in range of the targeted machine can be used to launch remote attacks over the Internet.
“Compromising the security of industrial remotes and machines would require transmission protocol know-how and the right tools. Launching a replay attack or e-stop abuse, for instance, would need only an appropriate device that costs a few hundred U.S. dollars,” Trend Micro researchers explained. “Meanwhile, attacks such as command injection, malicious re-pairing, and malicious reprogramming could require target equipment, which can cost from a hundred to a few thousand U.S. dollars. Attacker motivations may vary, but ultimately, significant business impact such as financial losses, system unavailability, and operator injuries could come into play as safety-critical machinery is involved.”
Trend Micro has published a research paper and a couple of videos summarizing the findings.
Related: Researchers Demo Remote Hacking of Industrial Cobots
Related: Industrial Robots Vulnerable to Remote Hacker Attacks














