Tripwire has analyzed the evolution of the security updates released over the past five years by Microsoft. The company determined that while the number of security bulletins has decreased, the number of vulnerabilities fixed with each bulletin has increased.
According to the security firm, Microsoft has started packing more vulnerabilities (CVEs) per security bulletin.
“CVEs represent vulnerabilities that have been discovered, and in Microsoft’s case (for the ones provided by the bulletins and Patch Tuesday), vulnerabilities that have been fixed,” explained Lane Thames, software development engineer at Tripwire. “So, the increasing number of CVEs (and CVEs per bulletin) shows that Microsoft is fixing more and more defects/vulnerabilities per unit time.”
The increase in the number of fixed security holes could be a result of code base growth. For applications that are still supported by Microsoft, the code base continues to grow, and as the number of lines of code increases, so does the overall defect rate, Thames said.
The number of vulnerabilities might also be increasing because of the software’s maturity. An increasing number of security researchers with advanced tools in their arsenal and a growing understanding of how Microsoft’s solutions inherit code from one another leads to more discovered vulnerabilities.
On the other hand, Tripwire warns that while white hat hackers identify more vulnerabilities, it’s likely that the same applies to black hats.
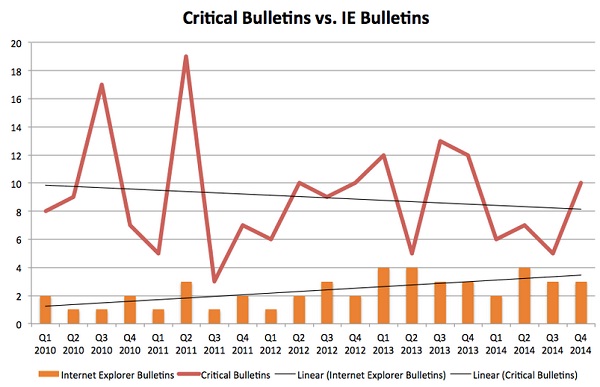
Over the past five years, the number of critical bulletins released by Microsoft has decreased, reaching 28 in 2014 — a new record low. While the number of critical bulletins has decreased, the number of Internet Explorer bulletins has increased over the last five years, Tripwire said.
The company’s analysis shows that close to half of the security bulletins released in 2014 covered vulnerabilities that could be exploited for remote code execution. As for the actual flaws, over three quarters of the ones patched last year could lead to remote code execution.
Microsoft seems to have its work cut out this year. So far, Google disclosed a total of three Windows vulnerabilities before Microsoft could fix them. Furthermore, a researcher released a proof-of-concept for a serious Internet Explorer vulnerability last week. The software giant says it’s working on addressing the bug but, according to the researcher, the company was informed of its existence in October.














