Researchers have discovered a new type of Man-in-the-Browser (MItB) attack that is Website independent, and does not target specific Websites, but instead collects data submitted to all sites.
This “universal” MitB attack, discovered by researchers at Trusteer, is different from traditional attacks, as it speeds up how data is stolen and may be used in automated campaigns.
 In a YouTube video (embedded below), the company demonstrated how the attack could happen. The video showed how a user could enter personal and financial information in a Web form on multiple Websites. After submitting the forms, the video showed a screenshot of the console used by the cyber-attacker. The console displayed the credit card data harvested from those sites, in what appears to be real-time data extraction.
In a YouTube video (embedded below), the company demonstrated how the attack could happen. The video showed how a user could enter personal and financial information in a Web form on multiple Websites. After submitting the forms, the video showed a screenshot of the console used by the cyber-attacker. The console displayed the credit card data harvested from those sites, in what appears to be real-time data extraction.
“uMitB’s ability to steal sensitive data without targeting a specific Website and perform real-time post processing removes much of the friction associated with traditional MitB attacks,” Trusteer wrote.
Traditional MitB attacks generally are triggered when the victim computer is infected with malware that can view all the data entered using the Web browser. Traditional attacks typically collect data such as login credentials, credit card numbers, and other sensitive pieces of information as they are entered into a specific site, such as an online banking portal or the login page of a Web service. Generally the malware has a specific list of Websites it is monitoring for data entry.
Harvesting data from other sites, or additional fields on the targeted site, generally requires some form of post-processing on the attacker’s side to parse the logs to extract the valuable data. That’s not to say that doesn’t happen, since parsers are easily available for purchase in underground markets, and some criminals simply sell off the logs in bulk to other criminals interested in the information, according to Trusteer.
However, universal MitB attacks don’t bother with a list of targeted sites but monitor any and all sites loaded in the Web browser, Trusteer found. It detects data entered in the browser regardless of the Website and uses “generic” real-time logic to parse each piece of information and save the relevant items when the form is submitted, according to Trusteer.
The stolen data is stored in a console controlled by the attacker before it is sold off to other criminals interested in the data, or used in other operations.
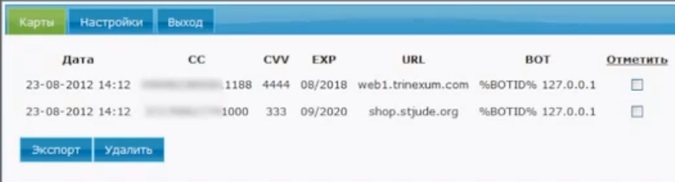
The ability of universal MitB malware to perform real-time processing on data being entered is “significant,” Trusteer said. One possible scenario has criminals automating credit card fraud by using universal MitB to steal credit card numbers and then feeding the freshly stolen information to carding sites.
“The impact of uMitB could be significant since information stolen in real-time is typically much more valuable than “stale” information, plus it eliminates the complexities associated with current post-processing approaches,” Trusteer said.
It appears that existing victims, those with machines already infected with the MitB malware, are susceptible to this new method of attack as soon as the malware gets updated with new configuration settings.
The best protection against these kinds of man in the middle and other fraud attacks is to secure the endpoint against malware, Trusteer recommended.
















