A recently uncovered piece of file-encrypting ransomware, which some believe may be linked to Iran, has been targeting processes and files associated with industrial control systems (ICS).
Written in the Golang programming language and dubbed Snake, the ransomware has been used in targeted campaigns aimed at enterprises. According to SentinelLabs, which has seen attacks involving Snake for the past month, files encrypted by this ransomware are difficult or impossible to recover without paying the ransom demanded by the attackers.
Snake targets a wide range of files, but avoids encrypting system files and folders. However, before it starts encrypting files, it attempts to terminate processes associated with various types of programs, including system utilities, enterprise management tools and even ICS.
SentinelLabs has mentioned Honeywell’s HMIWeb display builder and Israel-based industrial cybersecurity firm OTORIO says a majority of the industrial processes targeted by Snake are associated with products made by GE.
OTORIO says Snake terminates a critical process for the GE Digital Proficy server, which enables connectivity to the Proficy HMI/SCADA, Manufacturing Execution Systems (MES), and Enterprise Manufacturing Intelligence (EMI) systems. Terminating this process could cause serious problems for operational teams.
“The potential damage of a Snake attack is significant,” says Dor Yardeni, head of incident response and threat Hunting at OTORIO. “Deleting or locking targeted ICS processes would prohibit manufacturing teams from accessing vital production-related processes, including analytics, configuration and control. This is the equivalent of both blindfolding a driver and then taking away the steering wheel”.
Both OTORIO and SentinelOne have pointed out that the ransom note dropped by Snake instructs victims to contact the attackers at the email address “bapcocrypt @ ctemplar.com” to purchase the decryption tool.
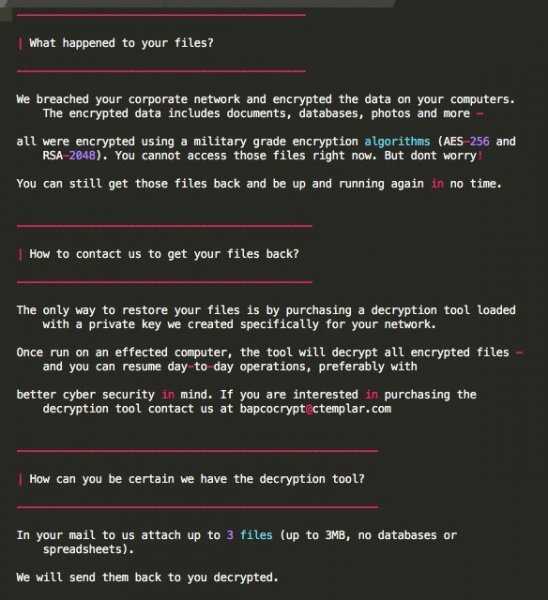
“bapcocrypt” may be a reference to the Bahrain Petroleum Company (Bapco), which hackers recently targeted using a piece of malware named Dustman. Dustman has been linked by Saudi Arabia’s National Cybersecurity Authority to ZeroCleare, a wiper that has been used to target energy and industrial organizations in the Middle East.
ZeroCleare has been linked to Iranian hacker groups, and experts believe Iranian threat actors could also be behind Snake. While SentinelOne says “there may very well be a relationship between the Snake and Dustman attacks,” OTORIO believes that Snake may have actually been used in an attack on Bapco.
Related: Realistic Factory Honeypot Shows Threats Faced by Industrial Organizations
Related: The Impact of Recycling on Industrial Cyber Security
Related: Hackers Behind Triton ICS Malware Hit Additional Critical Infrastructure Facility















