New Duqu Variant Discovered in Iran
It’s been an interesting week in developments related to Duqu, the complex cyber-espionage malware often referred to as “Son of Stuxnet.”
On Monday, Kaspersky Lab revealed details on what was a previously unknown programming language used in the “Duqu Framework”, a portion of the Payload DLL used by the Trojan to interact with Command & Control (C&C) servers after the malware infects a system. Kaspersky revealed that the Duqu framework was written using a custom object-oriented extension to C, generally called “OO C” and compiled with Microsoft Visual Studio Compiler 2008 (MSVC 2008).
On Tuesday, Symantec came forward with details on a file that it recently received, which after being analyzed, proved to be a new variant of W32.Duqu—the first new version of Duqu that Symantec has found this year. While the sample received by Symantec isn’t the full code used in the threat, it’s the key component needed to fully infect a system—the loader file that loads the full malware and stores it in an encrypted state on a system once it restarts.
The newly discovered Duqu variant came from Iran, Vikram Thakur, principal manager, Symantec Security Response told SecurityWeek.
The component received by Symantec (Driver file .sys) fits into the Duqu malware as illustrated here:
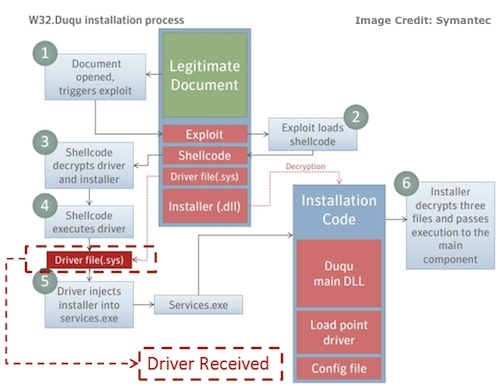
Symantec researchers also noticed changes in the encryption algorithm the malware authors used to encrypt other components of the threat on disk, as well as some differences in the driver file. “… the old driver file was signed with a stolen certificate—and this one is not,” Symantec researchers noted in a blog post. “Also the version information is different in this new version compared to the previous version we have seen. In this case, the Duqu file is pretending to be a Microsoft Class driver.”
Information on the command and control server that the sample would potentially use to connect to was not available in the new file, Thakur told SecurityWeek. “The author(s) changed the encryption algorithm they use to encrypt the other components on disk. Also the driver was changed to evade AV coverage. That leads us to believe development of Duqu is still ongoing,” he said.
While evidence of a new loader file shows the Duqu attackers are still hard at work, it’s unclear what else may have been updated or modified in the rest of the Duqu malware. “Without the other components of the attack it is impossible to say whether any new developments have been added to the code since we last saw a release from the group in November 2011,” Symantec’s blog post added.
This week’s developments show that in addition to knowing the authors behind Duqu are still at work, Duqu code is coming from a seasoned and experienced development team. In terms of the programming language used in the Duqu framework, there is no easy explanation as to why OO C was used instead of C++. Kaspersky Lab experts believe there are two likely causes that support its use: More control over the code and Extreme portability.
“These two reasons indicate that the code was written by a team of experienced ‘old-school’ developers who wanted to create a customized framework to support a highly flexible and adaptable attack platform. The code could have been reused from previous cyber-operations and customized to integrate into the Duqu Trojan,” noted Igor Soumenkov, Chief Malware Expert at Kaspersky Lab. “However, one thing is certain: these techniques are normally seen by elite software developers and almost never in today’s general malware.”
Duqu originally surfaced in October 2010 and has been the subject of considerable industry research as experts attempt to unveil more details on the mystery and origin of the malware. Duqu was designed to help attackers infiltrate systems via backdoor access and steal information and data primarily from industrial control systems and corporate secrets. While Duqu is assumed to have been created by the same authors as Stuxnet, unlike Stuxnet, it does not contain any components that attempt to control industrial control systems, but instead is primarily a remote access Trojan (RAT) designed to collect intelligence data and assets, possibly for use in future attacks.
Duqu – Designed to Be Resilient
According to Kaspsersky Lab, Duqu’s framework was written using code that was object-oriented and event driven, and performs its own set of actions making it ideal for network applications, and giving the malware a highly event driven architecture designed to be used in variety of conditions, including asynchronous commutations.
“This model makes sure that any form of communication can still occur even when some communications are already happening and could be taking a long time,” Roel Schouwenberg, senior researcher at Kaspersky Lab told SecurityWeek earlier this month. “Most programs out there hang or freeze if a certain operation is taking too long, much like your browser or email client may do at times. Using this asynchronous model means there’s no chance of that happening with Duqu.”
“The authors built an extremely resilient platform for that, ensuring Duqu, for instance, can still receive C&C commands while waiting for a response from another infected machine,” he added.
According to Symantec, the recently recieved Duqu component was compiled on February 23, 2012, indicating that the new variant has not been in the wild for long. “Checking the code we can see the authors have changed just enough of the threat to evade some security product detections, although this appears to have only been partially successful,” Symantec said.
“Although we do not have all of the information regarding this infection, the emergence of this new file does show that the attackers are still active.”
















