Two potentially serious vulnerabilities that could allow threat actors to cause significant disruption have been found in a widely used industrial connectivity device made by Moxa.
The Taiwan-based industrial networking and automation solutions provider has addressed the flaws.
 The two security holes, tracked as CVE-2022-2043 and CVE-2022-2044 and rated ‘high severity’, affect Moxa’s NPort 5110 device servers, which are designed for connecting serial devices to Ethernet networks. The vulnerabilities can be exploited by a remote attacker to cause the targeted device to enter a denial of service (DoS) condition.
The two security holes, tracked as CVE-2022-2043 and CVE-2022-2044 and rated ‘high severity’, affect Moxa’s NPort 5110 device servers, which are designed for connecting serial devices to Ethernet networks. The vulnerabilities can be exploited by a remote attacker to cause the targeted device to enter a denial of service (DoS) condition.
Moxa and the US Cybersecurity and Infrastructure Security Agency (CISA) have released advisories for the vulnerabilities. Moxa said only firmware version 2.10 is affected and instructed customers to contact its tech support department for assistance. CISA told impacted organizations to contact Moxa for a security patch.
Both Moxa and CISA have credited Jens Nielsen, a researcher at Denmark-based industrial cybersecurity company En Garde Security, for reporting the vulnerabilities.
In a blog post published this week, En Garde Security owner Mikael Vingaard said his company’s research department discovered the vulnerabilities in the first half of March 2022, when the vendor was provided proof-of-concept (PoC) scripts and videos showing exploitation.
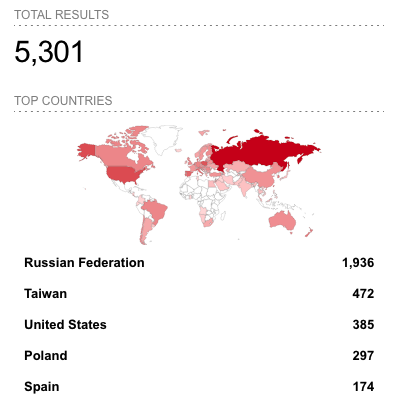
Vingaard told SecurityWeek that while Moxa NPort devices should not be exposed to the internet, in reality many are accessible from the web. A Shodan search shows more than 5,000 devices and while there may be some honeypots, Vingaard said they can’t all be honeypots.
He said exploitation of both vulnerabilities requires just a network connection to the targeted device. The exploits can be executed in ‘mere seconds’, and they can be automated and executed via the internet.
The impacted NPort devices are used worldwide, including in critical infrastructure sectors such as energy, critical manufacturing, and transportation systems. There have been reports that these types of devices were targeted for disruption in the 2015 attack on Ukraine’s power grid, which resulted in significant blackouts.
Learn more about vulnerabilities in industrial systems at
SecurityWeek’s 2022 ICS Cyber Security Conference
Exploitation of the vulnerabilities discovered by En Garde researchers could lead to the disruption of critical services in these sectors, with Vingaard describing the vulnerable Moxa devices as “a small part of the important infrastructural services to our society.”
He explained that the first DoS vulnerability can allow an attacker to cause the targeted device to stop responding to legitimate commands.
“The only way to regain control of the device would be to have staff power off/power on the device, which would require a person to be physically present,” Vingaard said. “This may often pose a problem in remote locations, where it could take significant time to get personnel on site, and not ideal in a situation where time to regain control may matter.”
The second vulnerability, an out-of-bounds issue, can allow an attacker to access and/or overwrite elements on the device, causing a crash or corruption of data. This can make the system become inoperable, in some cases possibly resulting in a permanently damaged device, Vingaard said.
Related: Moxa MXview Vulnerabilities Expose Industrial Networks to Attacks
Related: Flaws in Moxa Railway Devices Could Allow Hackers to Cause Disruptions
Related: Vulnerabilities in Moxa Networking Device Expose Industrial Environments to Attacks














