The number of US government domains for which TLS certificates were left to expire due to the government shutdown has now exceeded 130, UK-based cybersecurity solutions provider Netcraft reported on Wednesday.
A deadlock between President Donald Trump and the Democratic Party over funding for the controversial Mexico border wall has led to a partial government shutdown. The shutdown – the longest in US history – started on December 22 and it has entered its 26th day.
In addition to some online government services becoming unavailable – NIST’s Computer Security Resource Center (CSRC) is just one example – Netcraft revealed last week that agencies had failed to renew expired certificates for over 80 .gov domains, including ones belonging to NASA, the Department of Justice, the Court of Appeals, and the Lawrence Berkeley National Laboratory.
Allowing security certificates to expire not only makes websites inaccessible, it also makes them vulnerable to man-in-the-middle (MitM) attacks.
Netcraft says the number of impacted domains has now exceeded 130 and the list includes one belonging to the White House, pages.mail.whitehouse.gov, for which the certificate expired on January 15. Since this domain does not host any public services, the main problem is not that the address is inaccessible, rather that it could be leveraged by malicious actors in attacks aimed at White House staff.
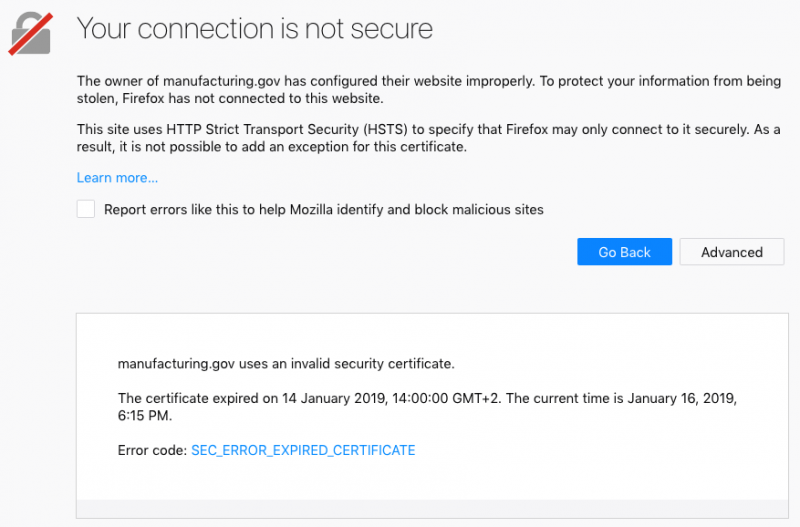
Manufacturing.gov and manufacturingusa.com, which host information on manufacturing programs, have also become inaccessible due to their shared certificate expiring on January 14. However, it’s worth noting that the websites can still be accessed if “www” is added to the address.
Other domains whose certificates have expired since Netcraft’s initial report belong to the Federal Aviation Authority, the National Archives and Records Administration, the Federal Financial Institutions Examination Council, and the Department of Agriculture.
Some of the impacted domains are on the HTTPS Strict Transport Security (HSTS) preload list, which means that web browsers such as Chrome, Safari, Firefox, Edge, Internet Explorer and Opera prevent users from accessing them if their certificate has expired. Websites that are not on the HSTS list can still be accessed by users by adding an exception in the browser’s “advanced” menu.
“Expired TLS certificates do not directly expose data, but when users visit the pages, they will be presented with an interstitial warning that the certificate is not valid,” Tripwire researcher Craig Young told SecurityWeek. “If strict transport security is not enabled, the user is able to click through the warning and visit the site. Since users are being told to expect these warnings, it makes the perfect opportunity for an attacker to intercept connections using a fake TLS certificate. The error message may have different details, but most users will not recognize this.”
“National adversaries are uniquely positioned to exploit this as they may have access to manipulate BGP records or otherwise influence telecom operations at a low level to redirect victim connections. In the last year, we’ve also seen evidence indicating that Russia has been developing and spreading router malware dubbed VPNFilter. This type of router implant is perfect for surreptitiously hijacking HTTPS connections to US government web sites,” Young added.
Related:Security of U.S. Government Sites Improved Only Slightly
Related: Many Federal Agencies Fail to Meet DMARC Implementation Deadline
Related: DMARC Use is Growing, But Difficult to Configure Correctly and Completely














