Microsoft has launched an investigation after a hacker group claimed to have stolen the source code of some of the tech giant’s products.
The cybercrime group named Lapsus$ made the claims. The same gang recently took credit for attacks on NVIDIA, Samsung, Vodafone, and Ubisoft, and in most cases the victims have confirmed suffering a data breach.
The hackers on Monday leaked 40 Gb of files allegedly belonging to Microsoft. They claim the files store source code for Bing, Bing Maps and the Cortana virtual assistant. The leaked files and folders are dated March 20, 2022.
“Bing maps is 90% complete dump. Bing and Cortana around 45%,” Lapsus$ wrote on its Telegram channel.
“We are aware of the claims and are investigating,” a Microsoft spokesperson told SecurityWeek via email.
Lapsus$ also claimed on Monday that it has targeted electronics giant LGE and identity and access management company Okta.
The hackers posted some screenshots apparently showing that they gained access to Okta customer accounts. They said they did not access or steal any database from Okta and instead targeted the company’s customers. Okta says it has hundreds of millions of users on its platform.
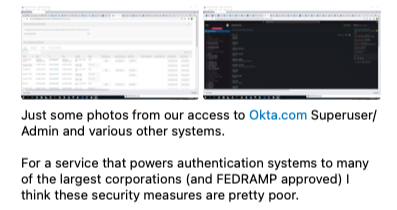
Bill Demirkapi, an offensive security expert who works at Zoom, has analyzed the screenshots, which appear to show the ability to reset employee passwords, unauthorized access to a company VPN, and superuser access to what appears to be an admin panel. One of the images displays the date January 21, 2022.
Indeed, in a statement to media, Okta confirmed detecting a cybersecurity incident in January, and the company believes the screenshots are related to that event.
“In late January 2022, Okta detected an attempt to compromise the account of a third party customer support engineer working for one of our subprocessors. The matter was investigated and contained by the subprocessor.” Okta said. “Based on our investigation to date, there is no evidence of ongoing malicious activity beyond the activity detected in January,”
In the case of LGE, the hackers leaked a file containing more than 80,000 usernames and password hashes allegedly associated with employee and service accounts.
SecurityWeek has reached out to LGE for comment and will update this article if the company responds.
Related: Microsoft Confirms ‘NotLegit’ Azure Flaw Exposed Source Code Repositories
Related: Microsoft: SolarWinds Hackers Attempted to Access Our Systems Until January 2021
Related: Windows 10 Source Code Leaked Online















