Users of Microsoft web applications such as Outlook or OneDrive don’t benefit from the level of privacy they may expect, a Chinese developer has discovered.
According to the developer, who goes by the name of ramen-hero, Outlook.com, OneDrive, and Microsoft’s account pages incorporate a unique user identifier known as CID in URLs. Unique to each user, the CID is a 64-bit integer associated with each Microsoft account and is used in Microsoft APIs for user identification.
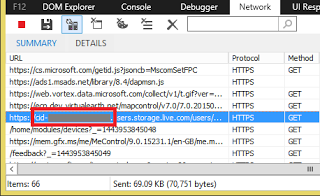
The issue is that because the CID is included in the host name part of the URL, it can be viewed by anyone monitoring the DNS traffic or with access to the web traffic of a user. This numeric identifier appears each time a user accesses Outlook.com, OneDrive, or the Microsoft account page, even if the request is made over an HTTPS connection.
 Microsoft leaking the CID in clear text allows bad actors to connect the company’s services to users, to grab a person’s account picture, view the display name attached to their account, and access information on when the account was created. On top of that, because the settings of some legacy apps such as Calendar are publicly accessible, bad actors could detect the location of a user.
Microsoft leaking the CID in clear text allows bad actors to connect the company’s services to users, to grab a person’s account picture, view the display name attached to their account, and access information on when the account was created. On top of that, because the settings of some legacy apps such as Calendar are publicly accessible, bad actors could detect the location of a user.
According to the Chinese developer, the CID is visible to anyone monitoring a person’s DNS traffic, including the local ISP, a government agency, or an attacker interested in monitoring the DNS traffic. Furthermore, the CID is visible to the exit node if the user connects to the Internet through Tor, and is also sent in clear text during TLS handshakes.
Users who linked their Microsoft accounts with their Skype accounts are further exposed, as bad actors knowing the main alias of a Microsoft account can also obtain the CID using the People app. The use of a HTTPS proxy server won’t help users either, as the host name containing the user identifier is visible to anyone with access to the web traffic log, the researcher said.
In a statement to SecurityWeek, a Microsoft spokesperson explained that the original web protocols have been designed in a manner that would allow applications to access public profile items. The company has already started to migrate Outlook.com mailboxes to Exchange Online, which uses a different protocol.
“The original web protocols were designed to allow applications to programmatically access public profile items. Non-public items are protected by user controlled authorization. Our recent protocols are more restrictive and over time we will phase out the older versions,” Microsoft’s spokesperson said.












