Microsoft this week released an out-of-band security update for its Endpoint Configuration Manager solution to patch a vulnerability that could be useful to malicious actors for moving around in a targeted organization’s network.
The vulnerability is tracked as CVE-2022-37972 and it has been described by Microsoft as a medium-severity spoofing issue. The tech giant has credited Brandon Colley of Trimarc Security for reporting the flaw.
In its advisory, Microsoft said there is no evidence of exploitation, but the vulnerability has been publicly disclosed.
Prajwal Desai has published a brief blog post describing the patch, but Colley told SecurityWeek that he has yet to make public any information and noted that he has been working with Microsoft on coordinated disclosure. The researcher believes that Microsoft’s advisory says the issue has been publicly disclosed because the tech giant is aware that he will talk about it at the BSidesKC conference this weekend.
The researcher expects a blog post detailing CVE-2022-37972 to only be published in November. However, he noted that it’s related to an issue described in a July blog post focusing on the attack surface of Microsoft System Center Configuration Manager (SCCM) client push accounts.
SCCM is the previous name of Microsoft Endpoint Configuration Manager (MECM), an on-premises management solution for desktops, servers and laptops, allowing users to deploy updates, apps, and operating systems. One method for deploying the needed client application to endpoints is client push installation, which enables admins to easily and automatically push clients to new devices.
In the July blog post, Colley showed how an attacker with admin privileges on one endpoint could abuse client push installation design flaws to obtain hashed credentials for all configured push accounts.
He warned that since some of these accounts could have domain admin or elevated privileges on several machines in the enterprise, they can be leveraged by threat actors for lateral movement and even as part of a disruptive ransomware attack.
The attack is possible, in part, due to a setting that allows connections to fall back to the less secure NTLM authentication protocol.
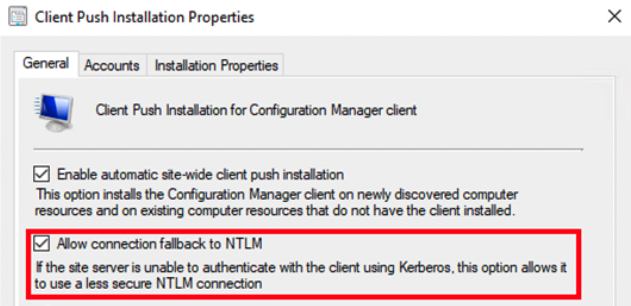
The MECM vulnerability patched this week by Microsoft with an out-of-band update is related to the use of NTLM authentication. The researcher explained that before Microsoft fixed the flaw, it was possible to force NTLM authentication for the client push account.
“Prior to this patch, it was possible for an attacker to bypass the NTLM connection fallback setting which was previously thought to have prevented the type of attack in my July blog,” Colley told SecurityWeek.
The US Cybersecurity and Infrastructure Security Agency (CISA) has urged administrators to review Microsoft’s advisory and apply the necessary updates.
Related: Microsoft Patch Tuesday: 84 Windows Vulns, Including Already-Exploited Zero-Day
Related: Already Exploited Zero-Day Headlines Microsoft Patch Tuesday
Related: Microsoft Confirms Exploitation of ‘Follina’ Zero-Day Vulnerability















