Operations at two major US-based chemical companies, Hexion and Momentive, were disrupted recently by a cyberattack reportedly involving LockerGoga, the ransomware that recently hit Norwegian aluminum giant Norsk Hydro.
In press releases published on Friday, Hexion and Momentive said they had been working on restoring networks and resuming normal operations after suffering “network security incidents” that prevented access to certain IT systems and data.
They both claimed that their manufacturing systems are on different networks and continued to operate normally with limited interruptions — the attack appears to have mainly impacted “corporate functions.”
Vice’s Motherboard reported that both companies were hit on March 12 by LockerGoga, the ransomware that recently also infected systems at Norsk Hydro. The theory that LockerGoga was involved in the attacks on Hexion and Momentive is based on a screenshot of a ransom screen obtained by the publication from an employee.
Both Hexion and Momentive are owned by the same investor group so it’s possible that their systems are connected and that is how the malware made it from one organization to the other.
SecurityWeek has reached out to Hexion and Momentive, but they both pointed to the press releases and refused to provide additional details.
According to Motherboard, which obtained an internal memo sent out to employees by Momentive’s CEO, the incident caused a global IT outage that forced the company to order hundreds of new computers and give some employees new email accounts as their old ones had become inaccessible.
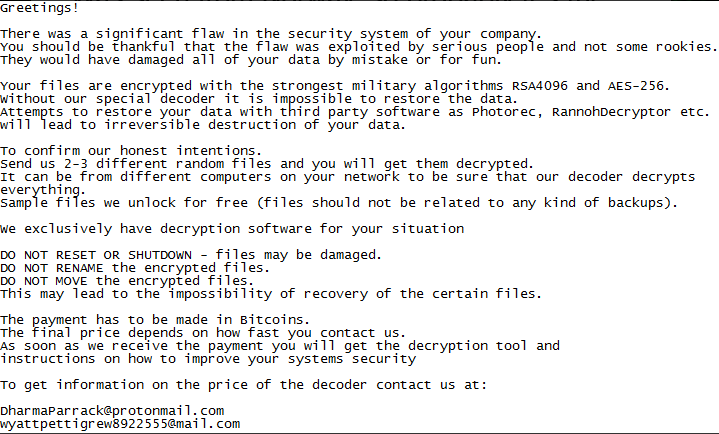
LockerGoga is designed to encrypt files, but it does not have any built-in mechanism for spreading on a network. In the case of the Norsk Hydro attack, experts believe it may have leveraged the organization’s Active Directory deployment to spread.
The Norwegian aluminum giant has been much more transparent about the attack and its impact — the company has provided daily updates about its efforts to restore affected systems.
The full extent of the impact is unclear in the case of Hexion and Momentive. Did the ransomware encrypt important data? Do the companies have good backups from which they can restore compromised files without paying any ransom?
Norsk Hydro said it did not plan on paying any money to the attackers. The company has been restoring systems using backups.
One of the first known victims of LockerGoga was French engineering consultancy Altran Technologies, which got hit in January. Researchers say there have been dozens of victims, and Hexion and Momentive were apparently targeted before Hydro.
Security expert Kevin Beaumont, who has been monitoring LockerGoga attacks, said — based on the number of unique malware samples uploaded to VirusTotal — that at least 8 organizations were hit. However, only four of them are currently known.
Researchers at MalwareHunterTeam have identified one LockerGoga sample on VirusTotal that was uploaded on March 12, which suggests that it may have been the one used in the attack against Hexion and Momentive.
Related: Industry Reactions to Norsk Hydro Breach
Related: Norsk Hydro Restoring Systems, But Not Paying Ransom












