Despite the increased deployment of DNS Security Extensions (DNSSEC), the global threats from phishing have continued to keep security professionals on their guard. The semi-annual “Global Phishing Survey” from the Anti-Phishing Working Group (APWG) provides powerful insight into what is happening in phishing worldwide.
As their name implies, the APWG endeavors to combat phishing on a global level. The APWG is a non-profit group comprised of professionals representing many industries; the mission of the APWG is to eliminate fraud, crime and identity theft — the byproducts of phishing, pharming, malware and email spoofing of all types.
The most recent report examines all phishing attacks detected in the second half of 2011. The data from those attacks was collected by APWG and supplemented by additional data from the China Internet Network Information Center (CNNIC) and other sources.
While I recommend all security professionals take time to read the survey, there are two important points that you should be aware of, even if you don’t read the full document.
First: phishing remains a major problem, even as it morphs into new shapes. Second: thanks to widespread and global collaboration, we’re making considerable progress toward eradicating phishing.
Trends in Phishing
Trend 1: Consolidation of Targets
In the most recent period that was tracked, the top 20 targets accounted for 78% of the world’s phishing attacks, and half of the targets were attacked only once or twice. The total number of targets dropped to 487, a drop of 17% from the comparable period one-year prior. Phishers now appear to be less interested in smaller targets and are concentrating instead on big ones. Previously, phishers mimicked a wider variety of sites. The primary reason for the shift seems to be that it is easier to sell stolen user credentials from more popular institutions.
Trend 2: Explosive Chinese Phishing Growth
The APWG also reported on the rise of Chinese phishing since 2010. The most recent period shows explosive increase in Chinese phishing — 81% more than in the comparable period one year ago, with over 22,000 targets attacked in the space of six months. That’s more than 100 new targets daily.
Taobao.com, one of China’s largest e-commerce sites, is now the world’s most popular phishing target, overtaking prior #1 Paypal. Like eBay and Amazon, Taobao specializes in business-to-consumer and consumer-to-consumer transactions. In the second half of 2011, there were 18,508 attacks against Taobao, representing 22 percent of all phishing attacks recorded worldwide. At the same time, the attacks against PayPal dropped dramatically, from 34,209 in the first half of the year to just 7,169 in the second.
Unlike most phishers, Chinese phishers don’t use many hacked domains. Instead, they prefer to set up their phishing pages on domains and subdomains they register themselves. Most domains are registered in the .TK (Tokelau) top level domain, which offers free registrations. Of the 18,508 attacks against Taobao, close to 40% used maliciously registered domain names.
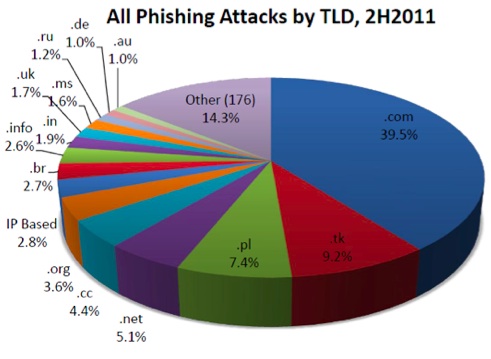
Trend 3: Plunging Phishing Uptimes
The first two days of a phishing attack are the most lucrative for a phisher, so quick takedowns are necessary to fight phishing properly. After reaching a high in the second half of 2010, the average uptimes for phishing attacks plunged in second half of 2011. The uptime of a phishing attack is an important factor in determining how damaging phishing attacks are and also can measure the success — or failure — of mitigation efforts. The longer a phishing attack remains active (“up”), the more severe the damage the victims and target institutions are likely to incur. Compared to an average up time of 73 hours in the second half of 2010, the average uptime for an attack in the same period a year later was 11 hours and 43 minutes. Unless you phish for a living, or rely on someone who does, that’s a shift that’s worth celebrating.
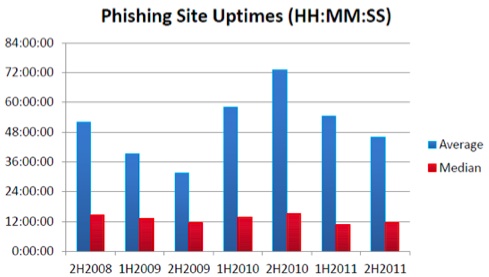
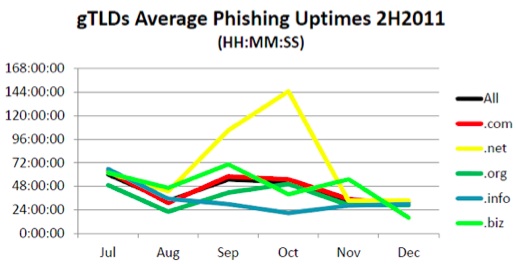
In the large generic top-level domains (gTLDs), .INFO and .ORG had the lowest uptimes, due to the aggressive notification and takedown programs at those registry operators.
Phishing is here to stay. While techniques for fighting these criminals are necessarily evolving along with the criminal activity itself, the lack of aggressive takedown programs and effective metrics and service levels has created a situation where criminals can depend upon cheap and poorly administered TLDs to wreak havoc on unsuspecting Internet users. As in all things digital, it pays to be careful before you click!









