Updated: 02/28/11 @ 11:58AM EST – A statement from the London Stock Exchange to SecurityWeek notes that the ads in question came from Unanimis, a UK ad network owned by Orange France Telecom Group. A representative from the London Stock Exchange said that the the Exchange’s website wasn’t impacted, but as a client of Unanimis it was flagged for malware alerts by Google. As a precaution, they have removed Unanimis-supplied advertisements. Unanimis claims a 73% reach in to the UK online population.
The Web Site for the London Stock Exchange (LondonStockExchange.Com) has apparenty been serving up malicious ads which could have resulted in users being infected with malware, according to a current Google Safe Browsing Report. Currently Google classifies the site as unsafe, and trying to visit the site using Firefox, Safari, or Chrome will result in a warning to the user. As of 7:32PM PST on Sunday, February 27th, the warnings were still being displayed.
According to Google’s Safe Browsing Report, “Of the 5 pages we tested on the site over the past 90 days, 1 page(s) resulted in malicious software being downloaded and installed without user consent. The last time Google visited this site was on 2011-02-27, and the last time suspicious content was found on this site was on 2011-02-26.”
Malicious software is hosted on 1 domain(s), including stripli.com/.
2 domain(s) appear to be functioning as intermediaries for distributing malware to visitors of this site, including unanimis.co.uk/, borsaitaliana.it/.
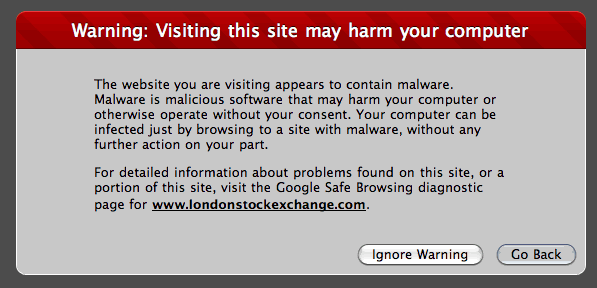
The site has NOT been hacked, and there is a big difference. The alert is likely a result of “malvertising“, a growing method for attackers to distribute malware via advertising tags served through an unsuspecting publisher’s Web site, blog comments, forums and other forms of user generated content, allowing cybercriminals to create content that can be used to carry out a wide range of malicious attacks.
Advertisers and agencies often utilize “third party ad tags”, allowing them to control and monitor their ads which removing the ability for publishers to be able to control what ads are served. With larger publishers, ad networks and exchanges having thousands of different ad tags running at any given time, monitoring all campaigns and creative being served is a challenge.
We will follow-up with a report once we are able to get additional details on what exactly flagged LondonStockExchange.Com to be identified as malicious.
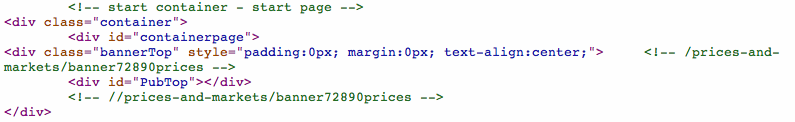
Update -7:16AM EST Monday: It appears as though the LondonStockExchange as a result of removing a top banner from the site that was previously showing 728×90 banner ads, the warnings are no longer showing. Looking at the site code, and the obvious blank space on the site, you can see where the code was changed to no longer serve the malicious banner ads which served via third party.