From hackers’ point of view, launching a successful attack, either malware based or through web application hacking, requires an investment in infrastructure. The infrastructure may take a physical form: Internet servers to host Command and Control servers (C2) and exfiltrated data, or be a logical asset: software hacking tools development, vulnerabilities research and stealth communication protocols definition.
Building an infrastructure is an investment, and like any other profit-oriented company, attackers want to maximize their Return on Investment (ROI) and get the most out of their initial investment. Today, we will discuss the two main approaches hackers take in order to capitalize on their investment and the derived security measures against each approach.
Mass Production Attackers
One possible strategy to maximize the ROI, is mass production. To maximize the revenue, the producer supplies the same product to as many customers as possible, or in the case of malware, infect as many users as possible using the same infrastructure. Mass production attackers are not interested in a specific target; they just want to hit as many targets as possible in order to monetize them.
When there’s no collaboration between defending parties, each new target has to react to the attack as if it’s new, while most chances other targets had already experienced the same attack in the past. Therefore, the security community has come to realize that collaboration between targets to associate a reputation score to resources is a crucial component in defense against mass production attackers. Community based reputation information has become paramount in all areas of security: E-mail sender reputation for SPAM filtering, C2 server addresses for infection monitoring, signatures of known malwares for malware detection and source reputation for web application attackers are only some examples.
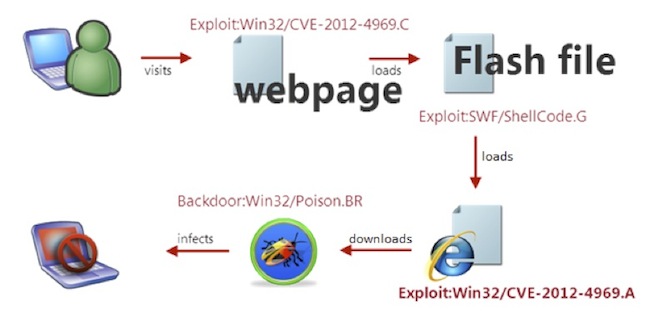
Figure 1 – An Infection Chain (Image Credit: Microsoft)
Mass production attackers are not blind to reputation based defenses and react to it by constantly changing their façade, i.e. changing the appearance of the infection chain with no radical changes to its substance. Such cosmetic changes include deploying new servers and creating new malware variants. The cost of such changes is relatively small compared to the initial investment, so mass production attackers pay it willingly in order to keep their business going. A good example for such ongoing battle between attackers and defenders is the Kelihos botnet. Kelihos was announced as dead by security companies several times, but it seems to keep on returning from the dead, equipped with new servers and new malware variants.
Currently, the most effective method to defend against such mass production attacks is to track the changes to the attack’s façade with some rapid reputation data updates. Therefore, end points that are protected by security solutions which receives a rapid reputation data updates are better protected against mass production attackers.
Boutique Attackers
Other hackers take a different approach. Instead of going after quantity, and attacking as many targets a possible, boutique attackers are going after quality and would only attack carefully selected, highly lucrative targets. These lucrative targets are corporations and more specifically their data: intellectual property (IP) and sensitive financial data. The damages for victims and the profit for such boutique attackers group, e.g. the notorious Chinese “Comment Group“, can be in the billions, as Coca Cola and many other corporations had found out.
As with mass production attackers, boutique attackers constantly change the façade of their attack. However, they do it, not as reaction to being caught by security companies but beforehand to avoid initial detection. For example, when launching a malware attack against a target they will send a phishing mail with a text that was not used in another campaign, from a new IP address with a slightly changed malware variant (checked against antivirus solutions to make sure they are not detecting it) and connects to previously unused C2 servers. By using a completely new infection chain, boutique attacker renders reputation based defenses useless.
Therefore, the defense against boutique attackers should be based on monitoring the assets they are after: the data. With data monitoring solutions, defenders can closely monitor access to their data, looking for non-standard behavior with respect to rate of access, amount of data being accessed or access patterns of machines in their network. Detecting these anomalies will prevent the stealing of the data.
Different Strokes for Malicious Folks
Although mass production and boutique attackers are technically very similar, the difference in their mode of operation calls for different defensive measures. While in the mass production attacks, defenders can learn from the experience of others and defend themselves with a rapid flow of reputation data, in the case of boutique attackers defenders can only rely on themselves and should use data protection solutions to detect anomalies in data access patterns.
As with any security issue, it can be best summarized with the eternal words of Sun Tzu: “If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle”.















