An Iran-linked cyberespionage group tracked as Elfin and APT33 continues targeting organizations in Saudi Arabia and the United States, Symantec reported on Wednesday.
Experts believe APT33 has been active since as early as late 2015. Since the beginning of 2016, when Symantec started monitoring its attacks, the group has targeted government, research, chemical, engineering, consulting, finance, manufacturing and telecoms organizations in the Middle East and other parts of the world.
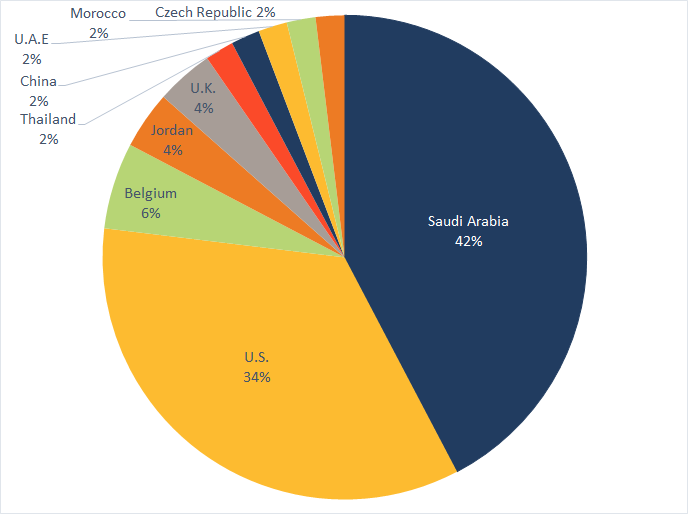
Of all the attacks observed by Symantec, 42% targeted Saudi Arabia, followed by the United States with 34%.
According to the cybersecurity firm, a total of 18 US-based organizations have been targeted over the past three years, including Fortune 500 companies. The list of US targets includes engineering, research, chemical, energy consultancy, IT, finance and healthcare organizations.
“Some of these U.S. organizations may have been targeted by Elfin for the purpose of mounting supply chain attacks. In one instance, a large U.S. company was attacked in the same month a Middle Eastern company it co-owns was also compromised,” Symantec researchers explained.
APT33 has used both off-the-shelf and custom-built malware in its attacks. The custom malware includes Notestuk (aka TURNEDUP), Stonedrill, and a backdoor written in the AutoIt language. The list of commodity malware includes Remcos, DarkComet, Quasar RAT, Pupy RAT, NanoCore, and NetWeird. The group has also used several publicly available hacking tools, such as Mimikatz, SniffPass, LaZagne, and Gpppassword.
Attacks launched by APT33 last month involved CVE-2018-20250, a recently disclosed WinRAR vulnerability that can be exploited to silently extract malicious files to arbitrary locations from an apparently-harmless archive file. The flaw can be exploited to extract a piece of malware to the Windows Startup folder, which helps attackers not only plant malware but also execute it.
This flaw was exploited by the threat actor in an attack aimed at a chemicals organization in Saudi Arabia. Other APT groups are also said to have leveraged the WinRAR vulnerability in their attacks.
In December 2018, researchers reported finding links between Shamoon 3, which had been used in attacks targeting the energy sector, and APT33/Elfin. At the time, Symantec reported that a Saudi Arabian organization hit by Shamoon had also been targeted by APT33, and McAfee suspected that this threat actor or someone impersonating it was likely behind the Shamoon 3 attacks.
“Because the Elfin and the Shamoon attacks against this organization occurred so close together, there has been speculation that the two groups may be linked. However, Symantec has found no further evidence to suggest Elfin was responsible for these Shamoon attacks to date,” Symantec said on Wednesday.
Related: Shamoon 3 Attacks Targeted Several Sectors
Related: Iranian Hackers Target Aerospace, Energy Companies
Related: Recently Patched WinRAR Flaw Exploited in APT Attacks















