Intel has launched its first bug bounty program and the tech giant is prepared to offer up to $30,000 for vulnerabilities found in its products.
The bug bounty program, hosted on the HackerOne platform, covers Intel’s software, firmware and hardware. It does not cover Intel Security (McAfee) products, the company’s web infrastructure, or acquisitions completed less than six months ago. Third-party and open source applications are also not in scope of the program.
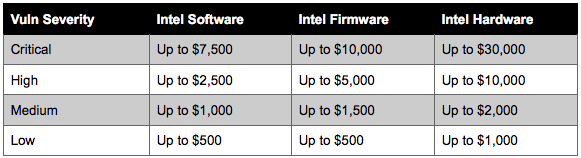
Researchers who find critical hardware vulnerabilities can earn a maximum of $30,000. Critical flaws in Intel software and firmware are worth up to $7,500 and $10,000, respectively.
The severity of a vulnerability is determined based on its CVSS 3.0 base score, and adjusted depending on the affected product’s threat model and security objectives.
“We want to encourage researchers to identify issues and bring them to us directly so that we can take prompt steps to evaluate and correct them, and we want to recognize researchers for the work that they put in when researching a vulnerability,” Intel said.
Following the recent Vault 7 leak by WikiLeaks, which describes the CIA’s alleged hacking capabilities, Intel announced the availability of a CHIPSEC framework module that can be used to verify the integrity of EFI firmware executables.
Microsoft launches new Office bug bounty program
Microsoft also made a bug bounty announcement on Wednesday. The company has launched a new program for Office Insider Builds on Windows.
This new bug bounty program, which runs between March 15 and June 15, promises payouts ranging from $6,000 to $15,000 for various types of vulnerabilities. Researchers can earn rewards if they find privilege escalation vulnerabilities via Office Protected View, flaws that allow macro execution by bypassing security policies, and code execution through a bypass of automatic attachment blocking policies in Outlook.
The announcement comes shortly after Microsoft decided to temporarily double bug bounty payouts for vulnerabilities found in core applications of the Office 365 suite.
Related: Researchers Use Intel SGX to Conceal Malware, Extract Private Keys
Related: Intel to Spin Off McAfee as Independent Security Firm
Related: New Intel Chips Pack Hardware Authentication Technology












