The Industrial Internet Consortium (IIC) has developed a new IoT Security Maturity Model (SMM), building on its own security framework and reference architecture. This week it has published the first of two papers: IoT Security Maturity Model: Description and Intended Use. This is primarily a high-level overview aimed at the less technical of IoT stakeholders.
“This is for the businessmen,” Ron Zahavi, chief strategist for IoT standards at Microsoft, told SecurityWeek, “to help them understand what is needed of security, and to help them translate that into a required maturity level for their own business.” The required maturity level becomes the target maturity level.
A second paper providing a more technical view for the security practitioners will be published in the summer. “The separation of the two,” said Zahavi, “allows different groups and verticals to develop specific profiles that can be published with the second technical document.”
The purpose of the model is to provide a single IoT SMM for all industry sectors, regardless of individual security requirements; and to be relevant to all IoT implementations, whether home, office or plant. The IIC’s guiding principles were to develop a new model suitable for all industries, to cover both process and technology, to leverage existing frameworks such as NIST and ISA-62443 rather than seek to replace them, to be simple and extensible, and to be suitable for use by all existing security assessment firms.
It starts from the basis that maturity is built on three primary dimensions: governance, enablement, and hardening. Each dimension comprises different domains. “Governance covers strategy and the operation and management of practices and process such as threat modeling and risk assessment, and supply chain management,” explained Zahavi. “Enablement includes the operation and management of traditional security technology, such as identity and access management, data protection, asset management, physical management, etcetera. Hardening,” he added, “is about the operational aspects of vulnerability and patch management, incident response and auditing, and so on.” In short, it is process, technology and operation.
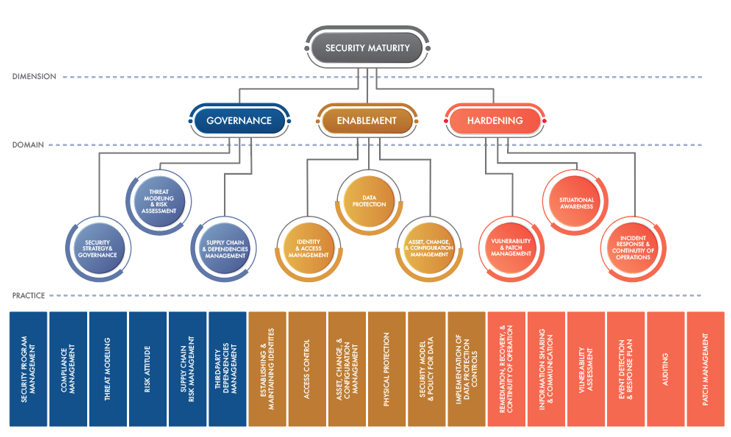
Each of the domains and practices is then evaluated on two axes: ‘comprehensiveness’ and ‘scope’. Comprehensiveness, said Zahavi, “is about the degree of depth and consistency that you apply security measures to the dimensions, domains and practices.” There are four levels (five, if you include ‘nothing’): minimal; ad hoc (where security tends to be reactive to a publicized incident or issue); consistent (using best practices and standards, and possibly centralized rather than spot solutions); and formalized (comprising a well-defined process for managing everything over time and with continuous improvement).
Scope is defined as the degree of fit to the industry or system needs. Here there are three levels: general (where there is no specific assessment of relevance to the specific IoT sector); industry specific (where security is implemented with regard to sector specific requirements – healthcare may be different to manufacturing); and system specific (where security implementation is aligned with the specific needs and risks of a particular system in a particular organization). For the system specific scope, Zahavi commented, “A retail organization might wish to delineate between its PoS sensors and its supply chain sensors.”
Combining the comprehensiveness and scope across the different practices allows an organization to define its IoT security maturity at both actual and target levels, and at a very granular level of the security implementation.
The target level of maturity is almost a statement of risk appetite. It is a business function, not a security function. For many years, security teams have operated blindly, with little communication between business and security. This is changing. The digitalization of industry and the merging of operational technology (the primary home of IoT devices) with information technology, and the subsequent exposure of IoT devices to the internet is changing the bottom line of security failures.
While the loss of information can be costly and brand-damaging, the loss of manufacturing can be catastrophic. The growth in ICS attacks and the dramatic effects these can have on profitability has got the attention of the board – and the board is now asking security to explain whether their IoT implementations are secure. Using the IIC SMM can help better align security with business priorities, and can help business and security come together.
Learn More at SecurityWeek’s ICS Cyber Security Conference
The recommended process is for business leaders to specify the maturity level targets, while the security team undertakes a current maturity assessment. The difference between the two levels can be assessed with a gap analysis from which a roadmap for closing any gaps can be developed. The roadmap should lead to any required security enhancements – which should then lead to a reassessment of the maturity level and a repeat of the process.
An aid to this process is a maturity profile template. The IIC hopes that different companies in different sectors will develop and publish high level IIC SMM maturity profiles that can be used by other organizations.
The intention of the IIC with this new IoT security maturity model is to augment, not replace, existing security frameworks. “There already exist accepted frameworks that get down to the control mechanisms for security,” explained Zahavi. “But if you look, for example, at the table of controls and the mappings in NIST, they don’t get into the level of ‘what do I do for my industry and what levels do I need to be in?’.
“What we’re doing,” he continued, “is we’re creating the higher-level maturity aspect of it, which is not met in all of those frameworks — we’re augmenting, we’re not replacing. For example, we don’t suggest specific required security controls. Instead, we’re mapping the SMM – and we’ll continue to do this (NIST, for example, is also an IIC member) – mapping practices and the appropriate maturity levels to existing frameworks and controls.
“So,” he said, “the intent is, if you have a profile for retail or healthcare or manufacturing, you should be able to look at your industry sector, and go back to those existing frameworks with a much narrower view of which mechanisms and controls you need to then deploy to achieve your target maturity for your own company in your own sector.”
The IIC IoT security maturity model is an aid to help companies employ existing favored security frameworks to reach their own defined target level of IoT security maturity.
Related: IIC Publishes Best Practices for Securing Industrial Endpoints













