According to a recently released report coming from the DHS-managed Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), U.S. companies that operate control systems associated with critical infrastructure have experienced a spike in what ICS-CERT calls “cyber incidents” in recent years.
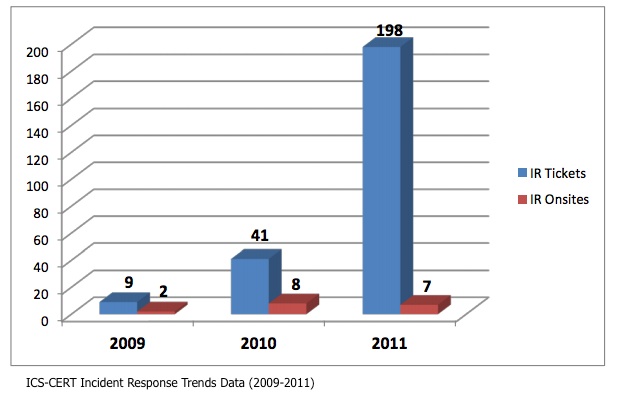
When ICS-CERT first launched in 2009, just nine incident reports were received, resulting in only four being confirmed as actual incidents.
Moving into 2010, ICS-CERT received 41 reports of incidents impacting organizations that own and operate control systems associated with critical infrastructure. In 2011 that number jumped to 198 reports.
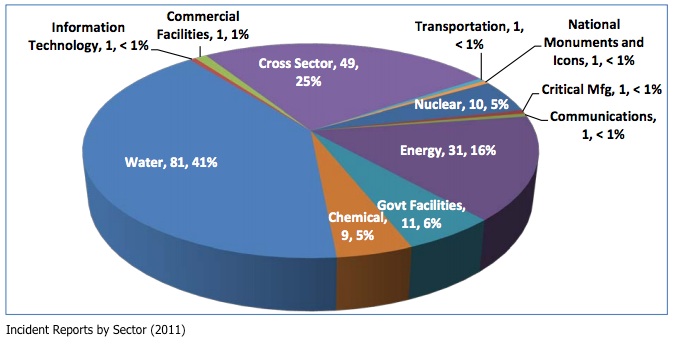
During 2011, the report highlights that incidents specific to the Water Sector, when added to those that impacted multiple sectors, accounted for over half of the incidents due to a large number of Internet-facing control system devices reported by independent researchers.
In terms of attack vectors, according to the report, the most common network intrusion vector was spear-phishing emails containing malicious links or attachments. Overall, Spear-phishing accounted for 7 out of 17 incidents that resulted in onsite deployment of ICS-CERT personnel, indicating that these tend to be the most damaging attacks. At least one incident involved an infection via a USB device, while sophisticated threat actors were present in 1 incident.
It’s also important to remember that these numbers are only incidents reported to ICS-CERT, and that many incidents never are reported to ICS-CERT, or even identified for that matter.
ICS-CERT notes that any critical infrastructure owner/operator can request its support with any cyber-related incident, and when appropriate get the assistance of an onsite incident response team to help with immediate mitigation efforts, provide cybersecurity threat briefings, and help with future defense strategies.
“A fundamental challenge utilities face is that supervisory control and data acquisition (SCADA) systems were not designed to be secure,” said Chris Petersen,CTO and co-founder of LogRhythm, speaking on the subject of recent ICS-CERT warnings. “Much of the existing infrastructure was developed and implemented prior to the rise of the Internet. Security was most often thought of in the physical sense.”
“The heat is on when it comes to protecting critical infrastructure in the United States. Unless the industry takes major steps to bolster its overall cyber security, 2012 could be the year hackers cause major disruptions that impact thousands of people,” Petersen added.
“Cybersecurity gaps can occur when personnel at all levels of an organization do not clearly understand security risks to the control systems environment,” the ICS-CERT report noted. “Cybersecurity gaps also can occur when personnel have an insufficient understanding of the technical impacts of inadequate security policies. Organizations often fail to develop common technical and security standards for the IT and control systems components of their environments. Without such standards, it may be impossible to create an effective security posture.”
The full Incident Response Summary Report is available here as a PDF download.













