
The U.S. Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has offered some advice on how antivirus software should be updated in industrial environments, but the recommended method is not very practical and experts warn that organizations should not rely only on antiviruses to protect critical systems.
ICS-CERT recommendations on updating AVs in industrial networks
ICS-CERT, a component of the Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC), coordinates security incidents involving control systems and facilitates information sharing in an effort to reduce the risk of cyberattacks. The organization’s latest Monitor newsletter provides some advice on how organizations should update their antiviruses in ICS environments.
“Antivirus software, when properly deployed and up-to-date, is an important part of a defense-in-depth strategy to guard against malicious software (malware),” ICS-CERT said. “Such software is widely used in Information Technology (IT) and ICS infrastructures. In business IT environments, it is common practice to configure each antivirus client to update directly from the antivirus vendor; however, because ICS and IT systems require separation by the ICS demilitarized zone (DMZ), ICS systems require different antivirus update methods.”
The ICS DMZ is the level between the enterprise zone and the control network. The DMZ, in addition to historians and remote access servers, can include the antivirus, Windows Server Update Services (WSUS), and patch servers.
Since the ICS DMZ is typically not allowed to communicate directly to the Internet, updating these services cannot be done automatically from the vendor’s server. One method for updating antiviruses on these systems is to manually download the update, copy it to a removable media drive, and then connect that drive to the machine needing the update.
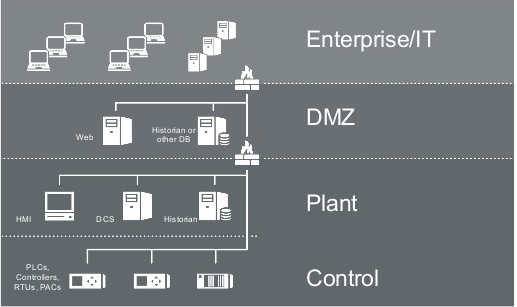
However, the process is not as straightforward as it sounds. ICS-CERT has advised organizations to first verify the source of the update, and then download the update file to a dedicated host. The file should be scanned for malware and its cryptographic hash needs to be verified in order to ensure it hasn’t been tampered with.
The removable media drive should also be scanned for malware and locked (i.e. prevent files from being written to it) once the update files have been copied. Before the updates are deployed on a production system, they should be tested and validated on a test environment that mimics production machines as closely as possible.
“This process is more labor intensive than an automatic chaining of updates, but it is not prohibitively time-consuming,” ICS-CERT said. “This ‘sneakernet’ method is common in air-gapped networks. Automatically ‘daisy chaining’ the updates, which is similar to the process used in many IT environments, is convenient but not recommended.”
Experts say the method is not very practical and AVs alone are not enough
SecurityWeek has reached out to several ICS security experts for comment on the recommendations from ICS-CERT.
Anton Shipulin, an ICS security expert with Kaspersky Lab, pointed out that while the sneakernet method does work for updating protection software in air-gapped networks, in practice, organizations are having difficulties keeping their systems updated. Kaspersky often finds outdated antimalware signature databases in the ICS networks analyzed during its assessments, Shipulin said.
“For the process to work, there should be good discipline in place to carry it out regularly, as well as a technically advanced endpoint solution – with capability to get updates from centralized on-premise update servers; it’s much simpler and faster to deliver updates only to a single point,” Shipulin explained. “It’s also worth mentioning that the same process should be a requirement for all OS, control systems and device software updates (with the agreement of ICS suppliers and vendors).”
Rick Kaun, VP of solutions at industrial cybersecurity firm Verve, noted that manually applying updates can be much more complicated than the process described by ICS-CERT.
“For example, not all AV updates are the same,” Kaun explained. “If you are under warranty support with a specific vendor for a specific AV function you not only need to download the AV file, you need to either get it from the vendor or at least confirm the vendor supports it. Further, many organizations may have multiple OEM vendors each with different AV solutions so you are needing to follow this practice for more than one set of files on different target systems – tracking and reporting of completion becomes a challenge.”
“Now let’s add into the mix the frequency at which AV files are generated. If they files are updated once a month this is likely manageable. If they are updated weekly this is more challenging. Now what happens when AV files get updated daily or even faster than that? What is your corporate stance on AV update frequency? This is an important consideration in deciding an appropriate balance between latest and greatest definition files (maximum protection) versus significant human effort (convenience/manpower),” Kaun added.
“There are very few organizations that are able to maintain the rigor and frequency of an AV program as outlined in the ICS article. It is well written and good advice but not overly practical in day to day application without significant dedication of manpower and/or automated tools,” Kaun said.
All the experts contacted by SecurityWeek agree that antiviruses should not be used – especially not on their own – to protect ICS. While industrial organizations are often concerned that security software could have a negative impact on their operations, modern solutions created specifically for ICS are designed to have minimal impact while still providing comprehensive protection. Furthermore, antiviruses cannot be installed directly on critical control devices, such as PLCs and DCSs. Modern products, however, passively monitor networks for any suspicious activity, regardless of the type of device targeted.
Patrick McBride, CMO at Claroty, pointed out that security products designed for IT environments should never be used in operational technology (OT) networks.
“AV has been proven ineffective and since it is not designed to work in OT environments, you need a Rube Goldberg process just to make ineffective stuff work poorly,” McBride said. “Unfortunately, some companies rely on outdated, ineffective AV solutions because various regulations require them.”
Dana Tamir, vice president of market strategy for Indegy, pointed out another interesting aspect. While antiviruses can provide partial protection, especially against known threats, the use of traditional antiviruses may not even be possible in some organizations due to the fact that many still rely on legacy systems such as Windows NT and XP in their ICS networks, and these legacy systems may not be supported by antivirus vendors, Tamir said.
This is confirmed by a recent CyberX study, which found that three out of four industrial sites are still running outdated operating systems in their ICS networks.
“[ICS-CERT’s advice] ignores the reality that many ICS environments aren’t installing any Windows security patches or running any AV protection whatsoever because of unsupported OSs like Windows 2000 and XP,” Phil Neray, VP of Industrial Cybersecurity at CyberX, told SecurityWeek.
Tamir also noted that an organization can install antiviruses on all managed computers, but if it doesn’t use a more comprehensive solution to monitor unmanaged endpoints, threats can make it into the organization’s ICS network via the devices brought in by integrators and consultants.












