Hundreds of industrial organizations have apparently received a piece of malware named Sunburst as part of the supply chain attack that hit IT management and monitoring firm SolarWinds last year, Kaspersky’s ICS CERT unit reported on Tuesday.
SolarWinds’ analysis of the attack revealed that up to 18,000 of its customers may have received trojanized updates for its Orion monitoring product. These updates contained the Sunburst backdoor, which gave the attackers access to victims’ systems, allowing them to deploy other payloads to organizations that represented an interest.
An analysis of command and control (C&C) mechanisms used by the Sunburst malware, specifically DNS responses, has allowed researchers to determine which organizations may have received Sunburst and which might have been breached further by the SolarWinds hackers.
Kaspersky’s industrial cybersecurity researchers analyzed a list of nearly 2,000 domains impacted by Sunburst and estimated that roughly 32% of them were associated with industrial organizations.
Learn More About Threats to Industrial Systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits Virtual Event Series
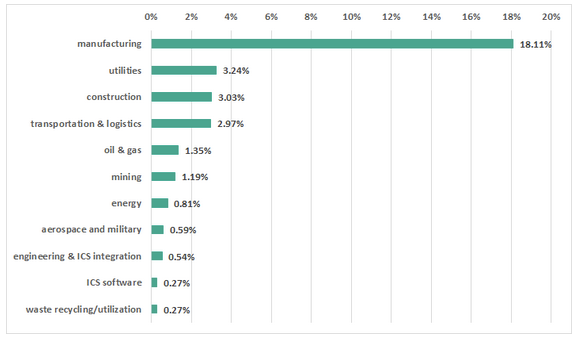
A majority of them are organizations in the manufacturing sector, followed by utilities, construction, transportation and logistics, oil and gas, mining, and energy. Kaspersky says they are located in various countries in the Americas, Europe, Asia and Africa, including the U.S., Canada, Iran, the Netherlands, Russia, Saudi Arabia and Uganda.
The cybersecurity firm has determined that roughly 200 of its customers received the malicious SolarWinds updates, including more than 20 in industrial sectors.
Continuous Updates: Everything You Need to Know About the SolarWinds Attack
“The SolarWinds software is highly integrated into many systems around the globe in different industries and, as a result, the scale of the Sunburst attack is unparalleled – a lot of organizations that had been affected might have not been of interest to the attackers initially,” said Maria Garnaeva, senior security researcher at Kaspersky.
“While we do not have evidence of a second-stage attack among these victims, we should not rule out the possibility that it may come in the future. Therefore, it is crucial for organizations that may be victims of the attack to rule out the infection and make sure they have the right incident response procedures in place,” Garnaeva added.
Three cybersecurity firms confirmed this week that they were impacted to some extent by the activities of the SolarWinds hackers, including Mimecast, Qualys, and Fidelis Cybersecurity.
Related: SolarLeaks: Files Allegedly Obtained in SolarWinds Hack Offered for Sale
Related: Class Action Lawsuit Filed Against SolarWinds Over Hack
Related: SolarWinds Taps Firm Started by Ex-CISA Chief Chris Krebs, Former Facebook CSO Alex Stamos












