Human resources giant Randstad last week revealed that its IT systems were targeted in a recent cyberattack involving a relatively new piece of ransomware named Egregor.
Netherlands-based Randstad is one of the world’s largest HR services providers, with more than 38,000 employees and operations in nearly 40 countries. The company claims it helped over 2 million people find a job last year and it reported a revenue of €23.7 billion ($28.7 billion).
Randstad said the incident impacted a limited number of servers and its operations have not been disrupted. However, it has confirmed that the attackers have accessed some data.
The cybercriminals behind the Egregor ransomware are known to steal data in addition to using the malware to encrypt the victim’s files, in an effort to increase their chances of getting paid. If a victim refuses to pay, the hackers either leak stolen data on a website that is accessible through the Tor network or they try to sell it to others.
“To date, our investigation has revealed that the Egregor group obtained unauthorized and unlawful access to our global IT environment and to certain data, in particular related to our operations in the US, Poland, Italy and France,” Randstad said in its statement. “They have now published what is claimed to be a subset of that data. The investigation is ongoing to identify what data has been accessed, including personal data, so that we can take appropriate action with regard to identifying and notifying relevant parties.”
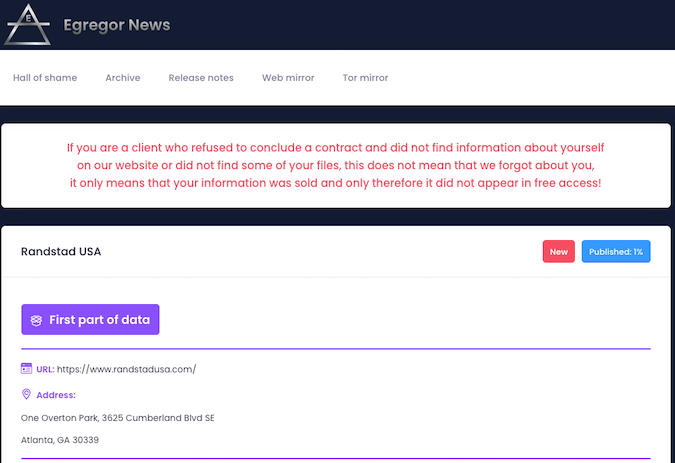
The hackers have so far released roughly 60Mb of information stolen from Randstad systems. The leaked files are mainly financial documents, mostly PDFs and Excel spreadsheets, which they claim represents only one percent of the stolen files.
The operators of the Egregor ransomware recently also targeted TransLink, the transportation agency of Metro Vancouver in British Columbia, Canada. TransLink has reportedly decided not to pay the ransom, but there is no mention of the company on the Egregor website so far.
Digital Shadows, a provider of digital risk protection solutions, whose researchers have been monitoring Egregor ransomware attacks, told SecurityWeek that the cybercriminals named 176 victims on their website between September 25 and December 2. A majority of victims are in the United States (82), followed by France (19), Italy (15) and Germany (9).
Related: University Project Tracks Ransomware Attacks on Critical Infrastructure
Related: IT Services Giant Sopra Steria Hit by Ransomware
Related: Canon Says Data Stolen in August 2020 Ransomware Attack















