A team of researchers from the Georgia Institute of Technology has demonstrated how, in theory, a malicious actor could manipulate the energy market using a botnet powered by high-wattage IoT devices.
Most botnets are powered by devices such as routers, cameras and DVRs. However, researchers from Princeton University warned a few years ago that threat actors looking to cause disruption to an energy grid could create a botnet of high-wattage devices, such as internet-connected ovens, air conditioners, and water and space heaters, which use 1-5 kilowatts of power.
The botnet described by the Princeton researchers, named BlackIoT (MadIoT), focused on causing disruptions, including local outages and large-scale blackouts, by simultaneously switching on and off the compromised high-wattage devices. However, the attack might not always be successful in practice, especially when the power grid protection mechanisms respond effectively to the shock caused by the botnet.
In the new attack method described by Georgia Tech researchers, which they have dubbed “IoT Skimmer,” the attacker uses a botnet of high-wattage devices to manipulate the electric market, either for financial profit or financial damage.
Most power markets include a day-ahead market, where participants purchase and sell electric energy with prices determined on the previous day, and a real-time market, which balances the difference between the actual demand for electricity and the day-ahead commitments.
The Georgia Tech researchers say a threat actor could manipulate the electricity market the same way financial markets can be manipulated: generate an event that causes prices to drop or rise, and buy when the price is low and sell when the price is high.
The researchers cited a report from the Federal Energy Regulatory Commission (FERC) in the United States that said there had been 16 potential market manipulation cases in 2018, with 14 of them closed without any action taken due to no evidence of manipulation being found. They also pointed to a recent attack on a British electricity market administrator.
The researchers believe that an attacker who has control of a high-wattage IoT botnet can slightly change demand in the power grid, thus impacting market prices.
One potential attacker could be a market player, which launches an attack in an effort to manipulate prices for their own profit. Another potential attacker is a state-sponsored actor, whose goal is to manipulate prices simply to cause the targeted country or targeted market players to suffer financial losses.
A nation-state attacker can obtain information on how market players are bidding — this data is publicly available — and influences real-time market prices for maximum economic loss.
The Georgia Tech researchers believe the gain of the attack is directly proportional to the number of bots within the botnet. The attack can be pulled off with as few as 50,000 bots with considerable financial impact.
The notorious IoT botnet Mirai was powered by 600,000 devices, but those were mostly low-wattage devices. However, the researchers told SecurityWeek in an interview ahead of a talk at the Black Hat cybersecurity conference, an attacker with large resources could create a botnet of high-wattage devices from scratch, by searching for vulnerabilities in the targeted IoT devices and then exploiting them in an effort to ensnare them in a botnet.
They pointed out that there are currently an estimated 30 million smart thermostats, which would give malicious actors plenty of potential targets, and the researchers anticipate that at one point in the future we will see such high-wattage botnets.
For an attack to be successful in the long term, it would have to be stealthy, and for that, the extra power consumption generated by the botnet would have to be within certain limits to avoid being detected by both the energy market and consumers whose devices are abused.
The difference between the predicted electricity load and the actual load is called the load forecasting error. If the changes generated by the attack are within the boundaries of this load forecasting error, the attack is unlikely to be detected by market operators and players.
As for avoiding detection by consumers, if the botnet turns on its devices for 100 days per year (or 8 days per month) for an average of 3 hours, the increase seen on the consumer’s bill would be of up to 7 percent, which the researchers believe is unlikely to be noticed by many users. However, this would still be enough for a significant attack.
In order to make the operation even stealthier, the threat actor could launch attacks on even fewer days, and they could turn on the compromised devices at strategic times of day (e.g. smart fridges in the middle of the day; EV chargers, ovens and dryers early in the morning). If the campaign is conducted by a market player, they could target competitors and even launch attacks that would affect them to some extent in order to throw off suspicion from themselves.
Since it would be illegal to create such a botnet and conduct real-world tests, the researchers used available data from the New York and California markets to calculate the efficiency of an attack.
For example, if a market player launches an attack, they could make an additional daily profit of $100,000 if they use a botnet of 150,000 bots — the size of the profit is directly proportional with the size of the botnet.
A state-sponsored threat actor could cause economic loss of $2 million per day with a botnet of 150,000 devices, while keeping the load profile within limits, the researchers said.
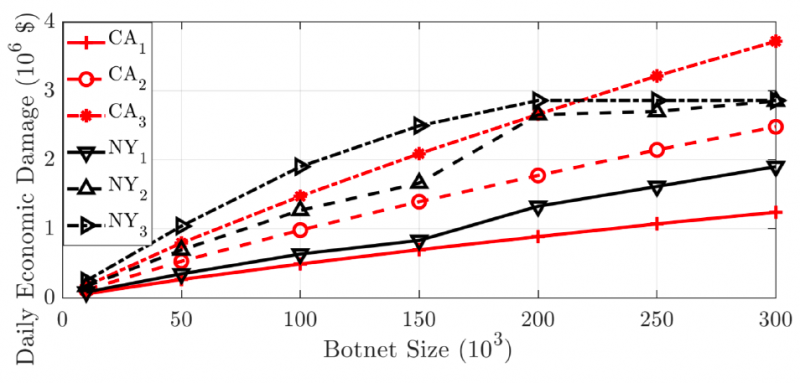
Based on their calculations, a market player could make an additional yearly profit of $24 million, while a nation-state group could cause economic damage of up to $350 million per year.
As for countermeasures against such attacks, the researchers propose the development of a real-time monitoring database that stores information on a small fraction of high-wattage IoT devices. This database would make it possible to detect potential attacks by looking for suspicious activity.
They also believe that market data should not be shared publicly — it should only be available to market players, and even they should only receive the data with a delay, not in real time.















