DigiNotar, the now defunct Netherlands-based Certificate Authority (CA) that suffered a breach resulting in fraudulent SSL certificates being generated, was completely at the mercy of a hacker that attacked them, a report delivered to the Dutch government explains.
DigiNotar, which was a subsidiary of VASCO Data Security before it was essentially hacked into bankruptcy, was left completely exposed, with the attacker having control over all eight (8) CA servers. Furthermore, the report notes that its entirely possible that rogue certificates still exist today.

The report, issued to the Ministry of the Interior and Kingdom Relations, shows that things were far worse than expected, ultimately proving that VASCO made the right decision in closing down DigiNotar. In addition to completely controlling the eight certificate servers, the attacker(s) altered log files in order to cover their tracks.
The final report was written by Fox-IT, the company that investigated the breach.
In a report published last year, Fox-IT said that some 300,000 Iranians were exposed as a result of the incident; and 531 fraudulent certificates were issued during the DigiNotar breach, including certificates for Google, Microsoft, MI6, the CIA, TOR, Mossad, Skype, Twitter, Facebook, Thawte, VeriSign, and Comodo.
Moreover, the earlier report said that the network setup and procedures at DigiNotar were not sufficiently secure to prevent the type of attack that occurred. Noting that DigiNotar’s network was severely breached, Fox-IT’s initial report revealed that all of the CA servers were members of a single Windows domain, which made it possible to access them all using one obtained user/password combination.
“The password was not very strong (Pr0d@dm1n) and could easily be brute-forced. The software installed on the public web servers was outdated and not patched. No antivirus protection was present on the investigated servers…No secure central network logging is in place,” the earlier report noted.
In the final report, all of these issues were explained as a domino effect that led to the total collapse of DigiNotar’s defenses, allowing a single attacker total control over its infrastructure.
What’s new however, is the detailed map of attack that is offered aftermath of Fox-IT’s painstaking investigation.
While DigiNotar kept its network divided into 24 internal segments, separated by an internal and external DMZ, the zones were not enforced and the firewall contained many rules that created exceptions for traffic between segments. The first point of entry by the attacker came from the external DMZ. Once that server was breached, the exception rules within the firewall policy allowed the attacker to exchange files between systems, and install scripts that acted as basic file managers.
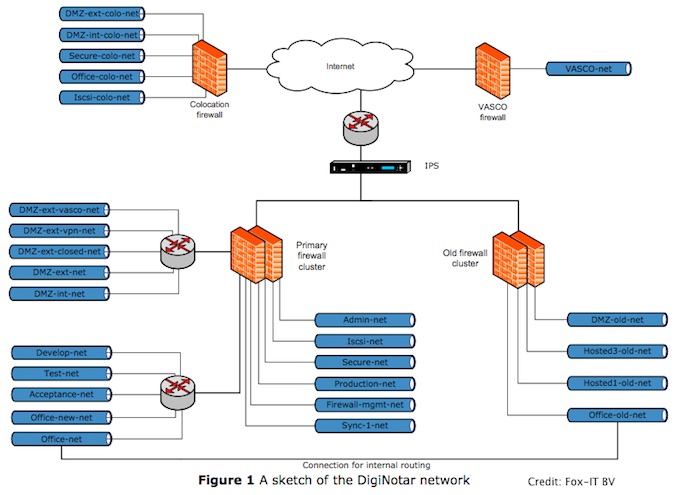
“The (recovered) log files from the Main-web server from the period of the intrusion showed a list of 12 internal and 21 suspicious external systems that connected to these scripts and a list of more than 100 unique filenames that were exchanged. Internal systems that requested these scripts were most likely to have been compromised, while external systems that requested these scripts were most likely used by the intruder to access DigiNotar’s network,” the final report explains.
The attacker then leveraged their access to move between segments, and install tools that enabled Internet connections to servers that were previously excluded from external access. This allowed the attacker to enable RDP (remote desktop) connections, which provided GUI access to the certificate systems.
“The investigation by Fox-IT showed that all servers that managed Certificate Authorities had been compromised by the intruder, including the Qualified-CA server, which was used to issue both accredited qualified and government certificates. In total, a non-exhaustive list of 531 rogue certificates with 140 unique distinguished names (DNs) and 53 unique common names (CNs) could be identified,” the report notes.
Unfortunately, as mentioned, the logging service for the CA management application ran on the same CA servers that were compromised. The investigation also showed that the attacker had full administrative rights and that database records on the CA servers were deleted or otherwise manipulated.
The 21-year-old Iranian hacker, who took responsibility for the DigiNotar attack, left his calling card in order to prove his claims. He is also the one behind a similar – though far less severe – attack on Comodo.
“I told all that I can do it again, I told all in interviews that I still have accesses in Comodo resellers, I told all I have access to most of CAs, you see that words now,” the hacker stated at the time.
“I thought if I issue certs from Dutch Gov. CA, they’ll lose a lot of money…But I remembered something and I hacked DigiNotar without more thinking in anniversary of that mistake. When Dutch government, exchanged 8000 Muslim for 30 Dutch soldiers and Animal Serbian soldiers killed 8000 Muslims in same day, Dutch government have to pay for it, nothing is changed, just 16 years has been passed.”
Fox-IT confirmed the hacker’s claims in its final report, noting that a “fingerprint that was left by the intruder was recovered on a Certificate Authority server, which was also identified after the breach of the Certificate Service Provider Comodo in March of 2011.”
After the breach made headlines, Microsoft, Mozilla, and Google revoked DigiNotar’s trusted status, pulling their root certificates from all of their products. Last September, the company filed for bankruptcy.
Fox-IT’s 101-page report is a highly detailed study of the breach. It’s a long, but worthy read. A full copy of the report in English is available here in PDF format.
Related: NIST Issues Guidance on Certificate-Based Breaches: Is Your Organization Prepared?













