Grammarly, the popular service for checking grammar and spelling, this week announced the launch of a public bug bounty program.
Grammarly has been running a private bug bounty program with HackerOne for more than a year. The program has nearly 1,500 participants and resulted in payouts totaling $50,000.
The company has now decided to make its program public – also via HackerOne – and it’s prepared to pay up to $3,000 for critical vulnerabilities. However, Grammarly says it may pay bonuses for unusual hacks, and rewards could be higher than expected if a report leads its internal security team to discover a more severe issue.
“Pricing is flexible, depending on the impact of the discovered vulnerability or for other instances such as a well-defined report or its automated version, which makes it easier to improve our internal testing framework,” Joe Xavier, VP of Engineering at Grammarly, told SecurityWeek.
The highest rewards are for critical vulnerabilities affecting Grammarly browser extensions, mobile keyboards, the Microsoft Office add-in, or the Desktop Editor.
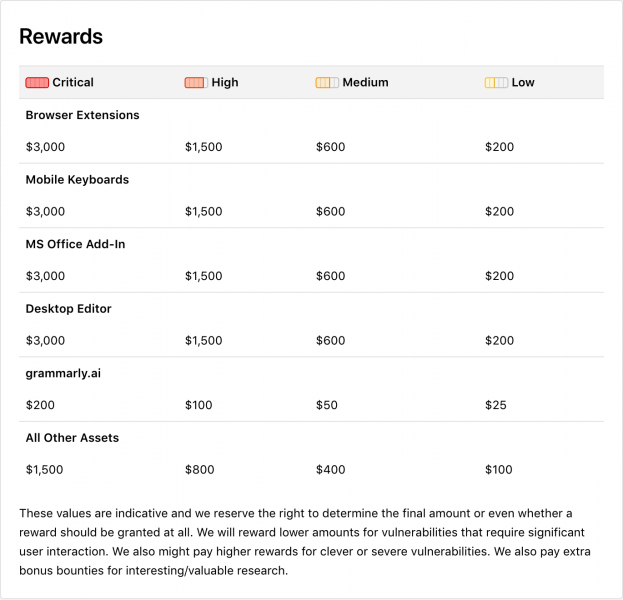
“We are open to various kinds of vulnerability reports, especially those that pertain to our native applications which carry a higher bounty,” Xavier explained. “With regards to specific threats, we are interested in CSRF, XXE and WAF break-in attack scenarios. We are excluding attacks that require physical access to a user’s computer.”
“We cover all our current product offerings for end-users with our public bug bounty program,” he added. “This includes the Grammarly Web editor, browser extensions (Chrome, Safari, Firefox, and Edge), native app for macOS and Windows, and mobile keyboard for iOS and Android.”
Earlier this year, Grammarly rushed to release patches for its browser extensions after Google Project Zero researcher Tavis Ormandy discovered a vulnerability that could have been exploited by malicious websites to access user data.
Related: U.S. Air Force Announces Third Bug Bounty Program
Related: HP Launches Bug Bounty Program for Printers
Related: Google Bug Bounty Program Now Covers Platform Abuse












