After several months of debate, Google has released its final proposal in the case of Symantec’s certificate authority (CA) business. All Symantec-issued certificates must be replaced by the time Google releases Chrome 70 next year.
Google announced its intention to take action against Symantec for improperly issued digital certificates in March. The announcement came after the company, particularly some of its subsidiaries and WebTrust audited partners, were caught wrongly issuing certificates.
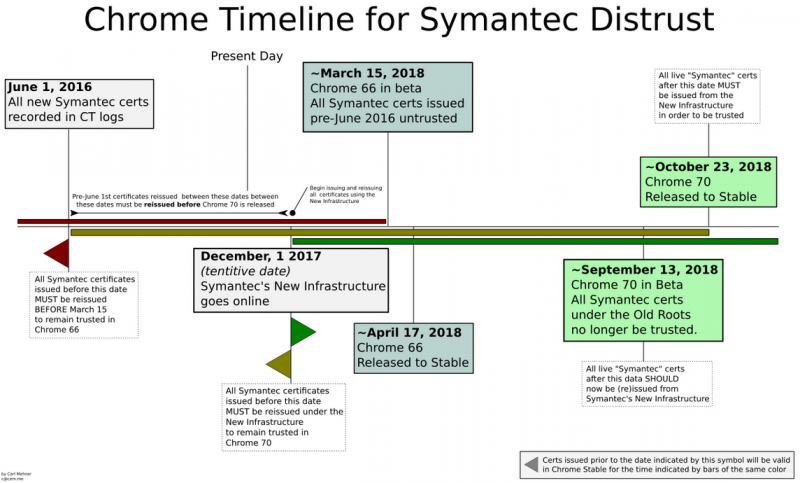
After several proposals on both sides, Google has come up with a final decision. According to the company, between now and March 15, 2018, websites using TLS certificates issued by Symantec before June 1, 2016, should obtain replacements from a trusted CA, including Symantec.
While Symantec will be allowed to release certificates, it will have to find a subordinate certificate authority (SubCA) whose infrastructure it can use. The company expects to have new infrastructure set up by December 1.
Starting with Chrome 66, currently scheduled for release on March 15, 2018, certificates issued on or after June 1, 2016, will no longer be trusted.
Certificates issued through Symantec’s old infrastructure after June 1, 2016, will continue to be trusted, but only until the release of Chrome 70. With the release of Chrome 70, scheduled for release on October 23, 2018, all certificates issued via the company’s old infrastructure will stop being trusted by the web browser.
Mozilla advised Symantec in May to accept Google’s proposal and described the alternative action it had been prepared to take in case an agreement was not reached. Microsoft and Apple have not made any comments on the matter, but based on the outcome of the case involving WoSign and StartCom, at least Apple is likely to follow in Google’s footsteps.
Symantec has promised to step up its game, but recent incidents have shown that the company, and particularly its subsidiaries, still have a long way to go. A researcher managed to trick Symantec’s RapidSSL into revoking TLS certificates by falsely claiming that their associated private keys had been compromised.
Related: Google Launches Its Own Root Certificate Authority
Related: Google Tells Symantec to Improve Digital Certificate Security