Open source Git repository management system GitLab this week announced the launch of a public bug bounty program with rewards of up to $12,000 for critical vulnerabilities found in its products and services.
GitLab aims to make software development easier and more efficient by providing an open source platform that can be used for the entire DevOps lifecycle. While in many ways it’s similar to GitHub, GitLab, which recently raised $100 million, offers a wider range of services.
The company launched a vulnerability disclosure program with the help of HackerOne back in 2014. Then, last year, it announced a small private bug bounty program that has resulted in a total payout of nearly $200,000 for roughly 250 vulnerabilities reported by more than 100 white hat hackers.
GitLab has now decided to launch a public bug bounty program via HackerOne. It covers the GitLab installation, production services, and the company’s other products, including its SaaS offering.
Researchers have been invited to report SQL injection, remote code execution, XSS, CSRF, directory traversal, privilege escalation and information disclosure vulnerabilities.
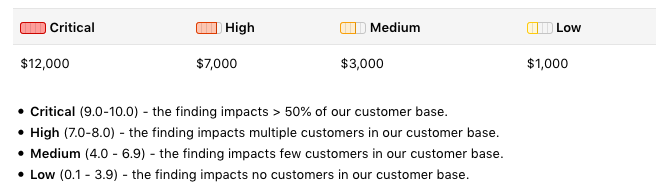
Critical vulnerabilities, findings that impact more than half of GitLab’s customer base, can earn researchers up to $12,000, while high-severity issues can be worth up to $7,000.
“GitLab is a cloud-native company,” said GitLab Director of Security Kathy Wang. “There is literally no physical office – all employees are remote, across 40+ different countries. Every third party product we use is SaaS-based. GitLab.com is hosted on Google Cloud. There is no firm perimeter, from a security perspective. We have to focus on access and credentialing management, as well as internal application security reviews, for example. Working with hackers helps the team scale, so that we can focus on other areas as well.”
One interesting vulnerability reported through the company’s private bug bounty program was disclosed in February. The flaw, which GitLab initially decided not to patch, could have been exploited to hijack users’ custom domains and point them to malicious content.
Related: Remote Code Execution Vulnerability Patched in Git
Related: Command Execution Flaw Affects Several Version Control Systems
Related: Hackers Can Use Git Repos for Stealthy Attack on Developers












